- Open Access
- Article
Navigating the Autonomous Era: A Detailed Survey of Driverless Cars
Vaibhavi Tiwari, School of Computing, Montclair State University, New Jersey, USA
* Author to whom correspondence should be addressed.
Journal of Engineering Research and Sciences, Volume 3, Issue 10, Page # 21-36, 2024; DOI: 10.55708/js0310003
Keywords: Driverless cars, autonomous vehicles, sensor, AI, V2X communication, SAE levels of automation, cybersecurity
Received: 11 September 2024, Revised: 12 October 2024, Accepted: 12 October 2024, Published Online: 22 October 2024
(This article belongs to the Special Issue Special Issue on Multidisciplinary Sciences and Advanced Technology 2024 & Section Engineering and Technology: Transportation Science & Technology (TST))
APA Style
Tiwari, V. (2024). Navigating the autonomous era: A detailed survey of driverless cars. Journal of Engineering Research and Sciences, 3(10), 21-36. https://doi.org/10.55708/js0310003
Chicago/Turabian Style
Tiwari, Vaibhavi. “Navigating the Autonomous Era: A Detailed Survey of Driverless Cars.” Journal of Engineering Research and Sciences 3, no. 10 (2024): 21-36. https://doi.org/10.55708/js0310003.
IEEE Style
V. Tiwari, “Navigating the autonomous era: A detailed survey of driverless cars,” Journal of Engineering Research and Sciences, vol. 3, no. 10, pp. 21-36, 2024, doi: 10.55708/js0310003.
The incorporation of cutting-edge technologies like sensor networks, artificial intelligence (AI), and vehicle-to everything (V2X) communication has hastened the rollout of autonomous vehicles (AVs), offering significant possibilities for the future of transportation. This document offers an extensive overview of AV technology, covering essential elements such as technological infrastructure, degrees of automation, cybersecurity threats, societal impacts, regulatory structures, and emerging trends. This analysis emphasizes the existing obstacles and progress within the industry by examining the activities of key entities like Tesla, Waymo, and General Motors. Additionally, a comparative examination of autonomous vehicles and drones is performed, providing distinct perspectives on possible cybersecurity vulnerabilities shared by both technologies, including GPS spoofing, jamming, and unauthorized data interception. This multifaceted approach highlights not only the existing vulnerabilities but also proposes proactive measures that can be implemented to reduce comparable risks across various AV platforms. The results highlight the necessity of establishing strong cybersecurity measures, overcoming regulatory challenges, and building public confidence to realize the complete promise of autonomous vehicles as secure, effective, and eco-friendly transportation options. This analysis provides an essential resource for comprehending the complex aspects of AV technology and its consequences, offering readers a comprehensive perspective on the challenges and opportunities within the autonomous vehicle sector.
1. Introduction
The automotive sector is swiftly progressing towards a future characterized by autonomous vehicles (AVs), with driverless cars at the forefront of this evolution. The vehicles utilize state-of-the-art technologies, such as intricate sensor networks, advanced artificial intelligence (AI), and real-time data processing, which together hold the potential to transform transportation by improving safety, efficiency, and convenience. Nonetheless, the incorporation of these complex systems brings forth significant cybersecurity is- sues that need to be tackled to safeguard AV performance and guarantee user safety.
Historically, autonomous vehicle research has spanned several decades, marking the transition of AVs from speculative fiction to a reality on our roads today. Experiments in this field began as early as the 1920s with Ralph Teetor’s invention of cruise control, and later expanded into semi-autonomous systems developed by Japan’s Tsukuba Mechanical Engineering Laboratory in the 1970s. These early projects laid the foundation for subsequent advancements, including Carnegie Mellon University’s Navlab and ALV projects, which achieved milestones in autonomous cross-country travel by the mid-1990s [1, 2, 3]. Government support, such as the United States’ $650 million allocation for the National Automated Highway System in the 1990s [4], further bolstered AV innovation, eventually enabling private industry players like Waymo, Tesla, and Nuro to lead commercial deployments from the late 2010s onward [5, 6].
In recent years, the concept of AVs has rapidly advanced due to technological progress, transitioning from controlled test environments to limited public road usage. Notably, McKinsey’s 2023 global executive survey highlights significant advancements, with insights from 86 decision-makers forecasting the commercial availability of Level 4 (L4) autonomous vehicles and robotaxis by 2030. Despite these advancements, substantial financial investments remain necessary. For instance, developing fully autonomous trucks and L4/L5 robotaxis requires over $4 billion and $5 billion, respectively [7]. This ongoing progress underscores the industry’s commitment but also highlights the resource- intensive nature of AV development.
This study uniquely contributes to the AV landscape by conducting a comparative analysis between AVs and drones. This comparison is particularly valuable because drones have encountered a wide array of cybersecurity threats. By examining these threats, the research explores how similar vulnerabilities could manifest within AV systems, thereby offering a basis for understanding potential misuse of AV technology. This insight allows for proactive mitigation strategies that can be applied to both AVs and drones, enhancing our overall preparedness against cyber threats.
However, the adoption of AVs at scale faces numerous hurdles, including regulatory, safety, and cybersecurity concerns. The cybersecurity landscape is especially complex, with threats such as remote exploits, unauthorized access, and adversarial machine learning attacks posing significant risks to AV systems [8]. The increasing reliance on wireless communication in AVs exposes them to attacks that could compromise vehicle control, sensitive data, and communication networks. The rapid evolution of cybersecurity risks between 2023 and 2024, such as adversarial attacks against AI systems and supply chain vulnerabilities, further emphasizes the need for robust cybersecurity protocols.
Beyond cybersecurity, AVs must also navigate regulatory and societal challenges. As the industry grows—projected to reach $556.67 billion by 2026—collaboration among auto- motive sectors, regulatory bodies, and researchers becomes essential to address the socioeconomic impacts, such as job displacement within driving-related industries. Trust- building initiatives, such as Waymo’s extensive road testing and Tesla’s Full Self-Driving (FSD) program, continue to play a critical role in driving public acceptance [6, 9, 10].
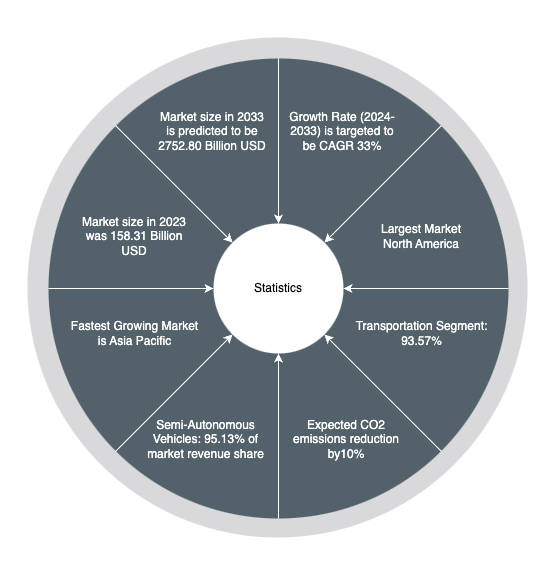
Through this study, readers will gain insights into AV technologies, the associated cybersecurity risks, and the broader societal and regulatory challenges. By presenting a detailed comparative analysis with drones, this research not only identifies shared vulnerabilities but also provides a framework for preemptive mitigation strategies. This exploration is intended to equip readers with a holistic understanding of AV technology, guiding them through the steps needed for safe, efficient, and socially responsible autonomous transportation. The projected growth trends [11] for the autonomous vehicle market are illustrated in Figure 1.
2. Motivation
There are a number of powerful incentives that are driving the development of autonomous vehicles. Each of these incentives addresses significant societal, economic, and environmental challenges respectively:
2.1. Enhancing Road Safety
An important driving force behind the development of autonomous vehicles is the ability to improve road safety by greatly reducing human error, which is a major contributor to traffic accidents. As per the World Health Organization, some 1.3 million individuals perish annually in road traffic accidents, with the bulk of these incidents being caused by human error [12, 13]. Driverless cars utilize sophisticated sensors, machine learning algorithms, and real-time data processing to enhance decision-making capabilities, sur- passing those of human drivers. This results in a decreased probability of accidents and a significant preservation of human life [14].
2.2. Increasing Transportation Efficiency
Through the optimization of vehicle movement and the reduction of the amount of time spent driving, autonomous vehicles have the potential to change the efficiency of transportation. It is possible for autonomous vehicles to establish contact with one another as well as with traffic management systems. This allows them to coordinate their movements, limit the number of occasions in which they are forced to stop and go, and determine the routes that are ultimately the most efficient. It is possible that these outcomes will result in greater traffic efficiency, decreased traffic congestion, and shorter travel durations [15, 16]. These outcomes are beneficial to individual commuters as well as the economy as a whole because they will increase productivity and decrease fuel consumption simultaneously [17, 18].
2.3. Reducing Traffic Congestion
Traffic congestion has a substantial impact on urban areas, leading to inefficiency in terms of time management, increased levels of pollution, and economic setbacks. Through the synchronization of their movements, the optimization of the timing of traffic lights, and the reduction of the need for parking spots in densely populated metropolitan areas, autonomous cars have the potential to alleviate traffic congestion. The integration of vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communication gives autonomous cars the capacity to dynamically adjust their speed and routes in order to avoid traffic congestion and maintain a continuous movement of vehicles. Such a feature allows autonomous vehicles to maintain a consistent movement of vehicles [19, 20, 21].
2.4. Improving Mobility for All
Autonomous vehicles have the potential to significantly improve the transportation alternatives available to individuals who are unable to operate a vehicle, such as the elderly, the disabled, or those who do not have their own means of transportation [22]. Individuals who may have difficulties with mobility can benefit from the on-demand transportation services provided by autonomous vehicles, which offer a reliable and convenient mode of transportation. This has the potential to improve self-sufficiency, facilitate access to essential services, and eventually lead to an improvement in the overall quality of life for the aforementioned demographics [23].
2.5. Contributing to Environmental Sustainability
The optimization of driving patterns, the decrease of idle time, and the encouragement of the use of electric vehicles (EVs) are all ways in which autonomous vehicles have the potential to improve environmental sustainability. Because they are able to operate more efficiently and eliminate excessive acceleration and braking, driverless cars have the potential to reduce the amount of fuel that is consumed as well as the emissions of greenhouse gases [24]. A large and infrastructure. Table 1 provides a brief overview of these technologies, highlighting the essential components used in each.
2.6. Economic Benefits
There is a high probability that the introduction of autonomous vehicles will result in considerable economic benefits. It is possible to realize significant cost savings in the areas of healthcare, emergency services, and vehicle repairs by reducing the number of accidents that occur on the roads. A large reduction in the number of accidents that occur in the United Kingdom, for instance, might result in savings of almost two billion pounds by the year 2030 at the very least [27]. Furthermore, it is predicted that the autonomous automobile industry will provide a multiplicity of employment opportunities in the areas of technological innovation, infrastructure advancements, and mobility services. This sector would also deliver more than £51 billion in economic benefits [28].
2.7. Accessibility and Inclusion
Autonomous vehicles have the potential to provide individuals with disabilities, the elderly, and other individuals who do not drive with enhanced mobility options, thereby boosting their freedom and general well-being [22]. Autonomous cars have the potential to be designed in such a way that they can accommodate a wide range of accessibility requirements, thereby offering a reliable and safe mode of transportation to all users.
3. Technologies Behind Driverless Cars
The technology used in driverless automobiles is varied and intricate, encompassing the integration of advanced sensors, artificial intelligence, vehicle-to-vehicle and vehicle-to- infrastructure communication, and sophisticated decision- making algorithms. These technologies collectively allow autonomous vehicles to accurately detect their surroundings, precisely determine their location, strategize safe routes, and efficiently navigate while interacting with other vehicles and infrastructure. Table 1 provides a brief overview of these technologies, highlighting the essential components used in each.
Table 1: An Overview of Technologies
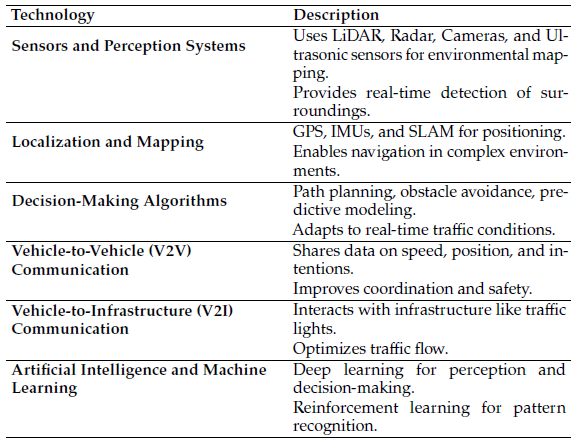
3.1. Sensors and Perception Systems
The powerful sensors and vision systems used in autonomous vehicles are central to their operational capabilities. These systems combine various types of sensors to collect and interpret data from the surrounding environment, generating a comprehensive view. LiDAR (Light Detection and Ranging) systems emit laser pulses, measuring the time it takes for them to reflect off objects, which helps create high-resolution 3D maps [29]. This is crucial for identifying the shape, distance, and size of obstacles, enabling precise environmental mapping and navigation. Radar sensors, which use radio waves to detect the distance and speed of objects, are essential for adaptive cruise control and collision avoidance, and are particularly effective in adverse weather where optical sensors may fail [30]. Visual cameras capture images of the environment that are processed using computer vision algorithms for tasks such as object recognition, lane detection, and traffic sign identification. Modern autonomous vehicles typically deploy multiple cameras to cover various angles, creating a complete visual representation of the surroundings. Ultrasonic sensors [31], primarily used for short-range detection, assist in parking maneuvers by detecting objects close to the vehicle, ensuring safety during low-speed operations. Collectively, these perception systems synthesize data from multiple sources to produce an accurate model of the vehicle’s surroundings, which is fundamental for decision-making and control activities.
3.2. Localization and Mapping
Accurate localization and mapping are essential for autonomous vehicle navigation, as they enable vehicles to determine their precise position and navigate complex environments. The Global Positioning System (GPS) provides basic positioning information, but in urban settings, where signal blockages by tall buildings can occur, GPS is often supplemented by other localization technologies. Inertial Measurement Units (IMUs) track the vehicle’s orientation and motion, supplying critical data for dead-reckoning and enhancing GPS accuracy. Simultaneous Localization and Mapping (SLAM) is another key technology, involving algorithms that build a map of the environment while simultaneously tracking the vehicle’s position within it. SLAM integrates data from LiDAR, cameras, and IMUs to produce detailed and accurate maps, which are vital for navigating dynamic and unfamiliar surroundings. Advanced navigation systems often employ a hybrid approach, combining fundamental maps with real-time perception data to adapt to immediate environmental changes [32]. Innovations from institutions like MIT’s CSAIL have even developed systems that rely on sparse topological maps and real-time sensor data, allowing autonomous vehicles to navigate without detailed maps.
3.3. Decision-Making Algorithms
Autonomous vehicles rely on sophisticated decision- making algorithms to interpret sensor data and execute driving tasks safely and effectively. Path planning algorithms determine the optimal route from the vehicle’s cur- rent position to its destination, using techniques such as graph-based search (e.g., A* algorithm) and optimization methods to ensure collision-free paths. These algorithms also dynamically adjust to real-time traffic conditions and obstacles [33]. Obstacle avoidance algorithms detect and navigate around obstacles with inputs from LiDAR, radar, and cameras, utilizing methods like Detection and Tracking of Moving Objects (DATMO) to forecast obstacle movements and adjust the vehicle’s path accordingly [33]. Additionally, predictive modeling anticipates the actions of other road users, such as pedestrians or other vehicles, by applying machine learning models, including deep neural networks, to enhance the accuracy of these predictions. Together, these decision-making processes enable the vehicle’s control system to analyze the environment, adhere to traffic rules, and ensure secure and efficient movement.
3.4. Vehicle-to-Vehicle (V2V) Communication
Vehicle-to-Vehicle (V2V) communication enables autonomous cars to share real-time information on their speed, position, and driving intentions. This exchange of data improves situational awareness and facilitates coordinated maneuvers, such as platooning, where vehicles travel in close formations to reduce aerodynamic drag and enhance fuel efficiency. V2V communication ensures precise coordination of speed and braking among platooned vehicles, which bolsters both safety and efficiency. Furthermore, V2V is crucial for accident prevention, as it allows vehicles to relay alerts about potential hazards, sudden stops, or other critical incidents [34].
3.5. Vehicle-to-Infrastructure (V2I) Communication
Vehicle-to-Infrastructure (V2I) communication involves interactions between vehicles and road infrastructure, such as traffic lights, road signs, and other smart systems. This technology plays a key role in optimizing traffic flow, as vehicles can receive real-time updates on traffic conditions, signal timings, and available detours, thereby reducing congestion and improving travel times. V2I communication also enhances road safety by providing vehicles with warnings about hazards, construction zones, or changes in road conditions. Integration with smart city infrastructure further extends V2I’s capabilities, enabling comprehensive traffic control and significant improvements in urban transportation [34].
3.6. Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are critical components of the architectures that enable autonomous driving. These technologies empower vehicles to learn from data, recognize patterns, and make decisions in complex situations. Deep Learning, for instance, is used extensively for visual perception, object recognition, and decision-making. Through deep neural networks, autonomous vehicles can process inputs from various sensors to detect objects, recognize traffic signs, and predict the actions of other road users. Reinforcement Learning, on the other hand, allows vehicles to learn from real-world driving experiences and continually enhance their performance. This adaptive approach enables autonomous systems to refine their decision-making processes over time and respond effectively to new environments. Overall, AI systems in autonomous vehicles facilitate the interpretation of sensory data, enable situational awareness, and support safe navigation without human intervention, improving their capabilities as they encounter diverse driving conditions.
4. Levels of Autonomy
4.1. SAE Levels of Automation
The Society of Automotive Engineers (SAE) has defined six levels of vehicle automation, from Level 0 (no automation) to Level 5 (full automation), which describe the degree of driver intervention required and the vehicle’s capabilities at each stage [35]. These levels provide a framework to understand the evolution and technical capabilities of AV systems:
- Level 0 (No Automation): At this level, the human driver is fully responsible for controlling the vehicle. While some technologies, such as warnings or momentary assistance (e.g., collision alerts), may be present, they do not control the vehicle.
- Level 1 (Driver Assistance): Basic driver-assist technologies, such as adaptive cruise control or lane- keeping assistance, enable limited control over either steering or acceleration/deceleration, but not simultaneously. Current technologies at this level often employ sensors and basic AI to interpret lane markings or maintain a safe following distance.
- Level 2 (Partial Automation): The vehicle can control both steering and speed under certain conditions, using a combination of radar, LiDAR, and camera systems to monitor the environment. Although the driver remains responsible for monitoring the road and staying alert, this level marks the transition to shared control.
- Level 3 (Conditional Automation): Vehicles at this level can manage all driving tasks under specific conditions, such as highway However, the driver must be ready to take over when the system requests. The transition between automated and manual control relies on advanced sensor fusion and environmental mapping, allowing the system to make decisions based on real-time data processing.
- Level 4 (High Automation): At this stage, the vehicle can perform all driving functions and monitor the environment in designated operational design domains (ODDs), such as urban areas or specific weather conditions, without driver intervention. While human oversight is not needed within the ODD, technological limitations prevent full autonomy under all conditions, with industry leaders like Waymo and Cruise currently testing Level 4 systems in pilot.
- Level 5 (Full Automation): This level represents the goal of fully autonomous vehicles, capable of per- forming all driving tasks in all conditions without any human intervention. The technical challenges include creating a robust infrastructure of AI, machine learning, and V2X communication, but full industry adoption remains unrealized as of 2024.
Industry Adoption and Comparison: While significant strides have been made in Levels 2 and 3, full Level 5 automation is not yet achieved. Currently, automakers and tech firms, such as Tesla and Waymo, are focusing on improving Levels 3 and 4 with varied strategies. Tesla’s approach, for example, relies heavily on computer vision and advanced neural networks for higher levels of autonomy, while Waymo incorporates high-definition mapping and extensive LiDAR systems. The comparative analysis within this paper explores these strategies, emphasizing how different companies prioritize elements like sensor fusion and machine learning to overcome the unique challenges at each automation level. By highlighting these approaches, the paper outlines key industry practices that contribute to the broader landscape of AV technology development [35].
4.2. Gradual Progression Towards Full Autonomy
The transition towards complete autonomy is slow, with cars now functioning at either Level 2 or Level 3. These levels enable vehicles to do specific driving tasks while still necessitating human supervision. The transition to higher levels of automation will be driven by notable progress in technology and legal frameworks. For instance, the testing and implementation of Level 3 systems such as Honda’s “Traffic Jam Pilot” and Mercedes-Benz’s Drive Pilot demonstrate encouraging advancements in minimizing human intervention in particular situations.
Autonomous vehicles must address various challenges before achieving full autonomy, including:
- Advanced Software and Mapping: Ensuring the software can handle diverse driving conditions and environment.s.
- Human Factors: Developing systems that can safely transfer control between human drivers and autonomous systems.
- Regulatory and Legal Frameworks: Establishing standards for liability, safety, and operation of autonomous vehicles.
- Ethical and Security Concerns: Addressing ethical dilemmas such as the “trolley problem” and ensuring robust cybersecurity measures.
The continued research and development efforts that are being made by industry leaders, government agencies, and academic institutions are absolutely necessary in order to overcome these hurdles and make progress toward completely autonomous vehicles.
5. Current State-of-the-Art
5.1. Industry Leaders and Major Players
Several important players who are at the forefront of developing and deploying autonomous vehicle (AV) technology are present in the industry of driverless cars, which is characterized by the presence of these key players. The following are notable businesses:
Tesla: Tesla has made great progress with its Full Self- Driving (FSD) software, which promises to provide full autonomy through continual over-the-air upgrades. This software has undergone significant development. Rather than relying on LiDAR, Tesla’s strategy makes use of a vision- based system that is equipped with cameras. Additionally, the company extensively depends on artificial intelligence and neural networks to interpret visual data.
Waymo: Waymo, which happens to be a part of Al- phabet Inc., is widely regarded as a pioneer in the field of autonomous vehicles. Waymo’s autonomous driving systems are able to reach a high level of precision and reliability thanks to the utilization of a combination of LiDAR, radar, and cameras. Waymo’s self-driving taxis, which are currently operating in Phoenix, Arizona, have delivered thousands of rides, in addition to providing critical data from the real world.
Uber: The Advanced Technologies Group (ATG) of Uber has been contributing to the development of autonomous vehicles (AVs) for its ride-hailing services. This group has been working on self-driving technologies. In order to enhance the safety and effectiveness of its autonomous systems, Uber has carried out extensive testing in a variety of metropolitan situations.
General Motors (GM) and Ford: GM and Ford, established car manufacturers, are making significant financial commitments to autonomous technology through their respective companies, Cruise and Argo AI. These firms are investigating several uses of autonomous vehicles (AVs), such as ride-sharing and delivery services, by utilizing their substantial knowledge and infrastructure in manufacturing.
5.2. Commercial Deployments and Pilot Programs
When it comes to the collection of data and the improvement of autonomous vehicle technology, commercial deployments and pilot programs are absolutely necessary. There are many noteworthy programs, including:
Waymo One: Waymo’s autonomous taxi service has been operational in Phoenix, Arizona, since December 2018, and recently expanded to San Francisco and Los Angeles. Within the confines of a geofenced area, this business offers trips that are completely autonomous to the general public, collecting vital data that may be used to improve their technology.
Tesla Full Self-Driving (FSD) Beta: Thousands of Tesla owners are participating in the FSD beta program, which is evaluating the software under real-world settings while it is being developed. Continuous feedback is provided to Tesla by this program, which enables incremental changes to be made to the capabilities of the FSD capability.
Cruise by GM: Cruise has been doing extensive testing of its driverless vehicles in San Francisco, with a particular emphasis on testing them in urban situations. In order to capitalize on General Motors’ manufacturing skills, Cruise intends to establish a commercial robotaxi service shortly.
Argo AI and Ford: A number of cities, including Miami and Austin, are participating in pilot programs that are being carried out by Argo AI in conjunction with Ford. Within the context of ride-sharing and delivery services, these activities are intended to improve the autonomous driving systems in preparation for their eventual deployment in commercial settings.
5.3. Technological Limitations and Challenges
In spite of the progress that has been made, autonomous cars continue to confront a number of technological restrictions and opportunities:
Complex Urban Environments: This is a challenge for autonomous vehicles because of the unpredictability and complexity of urban environments. The use of autonomous vehicles (AV) presents considerable issues in situations where there is a high volume of traffic, pedestrians, cyclists, and emergency vehicles.
Adverse Weather Conditions: The reliability of autonomous vehicles (AV) systems can be negatively impacted by weather conditions such as rain, snow, and fog, which can hinder the functioning of sensors like as cameras and LiDAR. The creation of reliable systems that are capable of functioning successfully in any and all weather circumstances continues to be a significant problem.
Cybersecurity: When it comes to protecting autonomous vehicles (AVs) against hacking and data breaches, it is necessary to provide comprehensive cybersecurity safeguards. Because of the high level of connectivity that exists amongst autonomous vehicles, any vulnerabilities that may exist could be exploited, which could result in the theft of important data or the malicious control of the vehicle.
Regulatory and Ethical Issues: A thorough regulatory framework must be developed in order to facilitate the broad use of autonomous vehicles (AVs). The establishment of standards for safety, liability, and insurance is included in this requirement. In addition, it is necessary to handle ethical conundrums, such as the process of making decisions in situations where accidents are unavoidable.
To summarize, although there have been notable progressions, it is imperative to do further research and development in order to surmount these obstacles and fully realize the capabilities of autonomous cars.
6. Existing Cybersecurity Threats
Driverless cars are equipped with a multitude of interconnected systems that manage everything from navigation to communication with external devices. These systems are susceptible to various types of cyberattacks, including:
6.1. Remote Exploits and Unauthorized Access
The dependence on wireless connectivity renders autonomous vehicles susceptible to remote exploitation. Unauthorised gain of access to the vehicle’s control systems by attackers has the potential to result in catastrophic failures. As an illustration, in 2015, security researchers Charlie Miller and Chris Valasek successfully conducted a remote hack on a Jeep Cherokee by taking advantage of weaknesses in its Uconnect smart entertainment system. Unauthorized access to the vehicle’s internal network was successfully obtained, enabling the delivery of commands to vital systems such as the engine, gearbox, and brakes. The cyber assault demonstrated that vehicles with unsecured connectivity might be influenced from any location, therefore giving rise to significant apprehensions regarding the security of autonomous vehicles [36].
6.2. Data Breaches and Privacy Concerns
Autonomous vehicles amass huge quantities of data, encompassing personal information as well as driving trends. Data breaches have the potential to result in the unauthorised acquisition and improper use of this confidential data. The 2016 Uber data breach, which compromised the personal data of 57 million passengers and drivers, highlights the possible hazards linked to the extensive data retention inherent in autonomous vehicles. Uber’s former Chief Security Officer, Joe Sullivan, endeavored to conceal the breach by offering the hackers $100,000 as part of a “bug bounty” scheme, resulting in severe legal repercussions [37].
6.3. Vehicle-to-Everything (V2X) Communication Attacks
Driverless cars communicate with infrastructure, other vehicles, and even pedestrians through Vehicle-to- Everything (V2X) technology. These communications are critical for safe operation but are vulnerable to various types of attacks.
In 2019, researchers demonstrated the feasibility of spoofing GPS signals to mislead autonomous vehicles, potentially causing them to veer off course or crash. This attack involves transmitting fake GPS signals that override the vehicle’s legitimate signals, leading to dangerous miscalculations [38].
V2X communication also relies on wireless signals that can be jammed, disrupting the flow of crucial information. In 2021, a jamming attack was demonstrated where multiple vehicles were rendered unable to receive or send data, causing significant traffic disruptions and even roadblocks. These incidents highlight the vulnerabilities in V2X communication protocols that could be exploited to create gridlock or force vehicles into unsafe conditions [39].
Additionally, relay attacks have been used to intercept and delay V2X messages, causing vehicles to react to out dated or incorrect information. This can lead to dangerous situations where vehicles may fail to stop at red lights or collide due to delayed braking signals [40].
6.4. Sensor Spoofing Attacks
Vehicle perception systems, including LiDAR, radar, and cameras, are vulnerable to sensor spoofing. Attackers have the ability to create deceptive signals that can be mistaken for genuine objects by these sensors. As an illustration, studies have shown that by projecting certain patterns onto road signs, the vehicle’s image recognition system can be tricked into misinterpreting the sign, which could result in risky decisions. In a similar vein, through the use of laser spoofing, malicious individuals have the ability to manipulate LiDAR readings. This can result in the creation of deceptive obstacles or the concealment of genuine ones [41].
6.5. Malware and Software Exploits
Vehicle software can be targeted by malware attacks that take advantage of weaknesses in the operating system or third-party applications. As an example, in 2018, a group of experts made an important finding regarding a vulnerability in Tesla’s Model S. This finding enabled them to remotely control the vehicle. The attack was carried out by taking advantage of a vulnerability in the vehicle’s browser, which enabled the researchers to insert harmful code. Once inside, they had the ability to control various aspects of the car, including unlocking doors and even steering [42].
6.6. Man-in-the-Middle (MitM) Attacks
Intercepting and potentially altering communications between the vehicle and external systems is a common occurrence in MitM attacks. In 2020, a groundbreaking discovery was made when experts successfully showcased a method of intercepting V2X communication, resulting in a potential vulnerability for Tesla vehicles. The manipulation of sensor data led to the vehicle misinterpreting its surroundings. Such an attack has the potential to result in the vehicle receiving inaccurate information, such as incorrect speed limits or traffic signals, which can lead to unsafe driving behavior [43].
6.7. Denial-of-Service (DoS) Attacks
Denial of Service (DoS) attacks aim to incapacitate a vehicle’s systems or communication channels by inundating them with excessive traffic. In a recent experiment con- ducted in 2019, a group of researchers successfully demonstrated a disruptive attack on a fleet of autonomous vehicles. The attack involved overwhelming the vehicles’ communication channels with an excessive amount of traffic, causing them to experience a denial-of-service (DoS) situation. This incident resulted in a total disruption of vehicle-to-vehicle (V2V) communication, resulting in a breakdown of synchronized driving and the possibility of accidents [44].
7. Emerging Threats in 2023-2024
Recent advancements in AI and machine learning have introduced new dimensions to cybersecurity threats in driverless cars. The following are some of the most concerning threats identified in the past year:
7.1. Adversarial Machine Learning (AML) Attacks
As driverless cars increasingly rely on AI to make real- time decisions, they become targets for adversarial machine learning (AML) attacks. These attacks exploit vulnerabilities in AI models by introducing carefully crafted perturbations to the input data. These perturbations, often imperceptible to human observers, can cause the AI to make incorrect decisions, such as misclassifying road signs or obstacles. For instance, in 2023, researchers demonstrated that by placing inconspicuous stickers on stop signs, they could cause AI systems in driverless cars to misinterpret them as yield signs, leading to potentially dangerous outcomes. The technical complexity of AML attacks lies in the ability to generate perturbations that evade detection while consistently fooling the model across various scenarios, making them a significant threat to the safety and reliability of autonomous vehicles [45].
7.2. Supply Chain Attacks
The global supply chain for automotive components is vast and interconnected, making it a prime target for sophisticated cyberattacks. In 2024, a major automotive supplier was compromised through a multi-stage attack that involved the insertion of malware into firmware up- dates for critical components used in driverless cars. The malware was designed to remain dormant, undetected by traditional security measures, until specific conditions were met, at which point it would activate and allow remote attackers to take control of the affected vehicles. This attack exemplifies the growing complexity and reach of supply chain threats, where the integrity of software and hardware components can be compromised at any point along the supply chain, from manufacturing to distribution. The challenge in defending against these attacks lies in the need for comprehensive verification processes and the integration of secure development practices across all tiers of the supply chain [46].
7.3. Ransomware Targeting Vehicle Systems
Ransomware targeting AI-driven and autonomous vehicles represents an emerging cybersecurity challenge due to the complexity and connectivity of these systems. Such attacks could exploit vulnerabilities in the vehicle’s software stack, potentially locking down critical systems like navigation, braking, or powertrain control. By encrypting the vehicle’s control systems, ransomware [47] can render the car inoperable until a ransom is paid, usually in cryptocurrency. The decentralized nature of these attacks makes them difficult to trace, and the integration of AI increases the risk, as machine learning models can be manipulated or disrupted to exacerbate the impact. Additionally, the connected ecosystem of vehicles, with constant communication to cloud services and other devices, introduces multiple attack vectors, such as over-the-air updates, that can be compromised. This highlights the urgent need for multi-layered security strategies, including robust encryption, anomaly detection systems, and secure software development practices to mitigate these risks [48].
7.4. Keyless Car Theft and Relay Attacks
The advent of key less entry and ignition systems in modern vehicles has introduced new security vulnerabilities in the automotive industry. These conveniences have become targets for sophisticated theft techniques, particularly man-in-the-middle attacks. Such attacks exploit the communication between cars and key fobs, allowing thieves to unlock and start vehicles without triggering alarms [49]. In 2023, the discovery of Bluetooth relay attacks on Tesla vehicles highlighted another critical weakness. This exploit took advantage of vulnerabilities in Bluetooth Low Energy (BLE) protocols used in passive entry systems. By relaying Bluetooth signals, attackers could access vehicles without the physical presence of the key fob. Although Tesla addressed this specific issue with a software update, the incident underscored a broader cybersecurity challenge [50].
7.5. Risks in Autonomous Vehicle Charging Infrastructure
As electric vehicles (EVs) have evolved, cybersecurity vulnerabilities in their charging infrastructure have become a significant concern. These issues are even more critical for autonomous vehicles (AVs), which also rely on secure data exchange with charging stations. The increased complexity and autonomy of AVs heighten the risks, including the potential for malware, fraud, remote manipulation, and disabling of charging stations. These vulnerabilities pose serious threats to the safety and integrity of the autonomous vehicle ecosystem [51].
7.6. Causing Traffic Jams
The interconnected nature of autonomous vehicles makes them vulnerable to coordinated cyberattacks that could lead to significant traffic disruptions. By compromising the control systems of multiple driverless cars simultaneously, an attacker could create artificial traffic jams. For instance, cars could be programmed to slow down or stop in strategic locations, blocking key intersections or highways [52]. Such disruptions could be used as a form of protest, to create chaos in urban environments, or as a precursor to other criminal activities, such as facilitating the escape of criminals from law enforcement by creating diversions.
7.7. Noise Pollution
In recent events, San Francisco residents experienced disturbances due to Waymo’s autonomous vehicles persistently honking in residential areas during nighttime hours. This unexpected behavior, initially captured on video by local residents, drew significant public attention and prompted Waymo to respond with an apology and immediate corrective measures. According to Waymo, the honking feature was originally designed to minimize collision risks on public roads by signaling to other vehicles and pedestrians. However, when applied in confined parking areas, the feature led to excessive noise pollution, particularly during early morning hours, causing distress to the community [53]. This incident not only highlights the complexities and unintended consequences of deploying autonomous vehicles in urban environments but also raises concerns about potential misuse. Autonomous vehicles’ honking functions could be exploited by cybercriminals to create targeted noise pollution in densely populated areas. If an AV system were to be compromised, attackers could manipulate honking or other sound features, intensifying urban noise pollution and causing widespread disruption. This example underscores the need for robust cybersecurity measures that address not only operational functionality but also safeguard against potential abuses that could impact public well-being. As AV technology continues to advance, these considerations will be crucial for ensuring harmonious integration within urban settings.
8. Countermeasures for AV Cybersecurity Threats
Autonomous vehicles (AVs) encounter various cybersecurity threats that can jeopardize their safety, operational capabilities, and the confidence of the public. This section examines essential strategies aimed at reducing these risks through the improvement of AV system security against a range of potential attacks.
8.1. Adversarial Machine Learning (AML) Attacks
Adversarial Machine Learning (AML) attacks exploit weaknesses in AI models, causing them to make incorrect decisions. To counter AML attacks, AV developers can utilize several advanced defense techniques:
- Adversarial Training: This technique involves training AI models on adversarial examples—data intentionally perturbed to mislead the model—so that the model learns to recognize and resist such By exposing the model to these adversarial inputs during training, its robustness against real-world attacks is improved [54].
- Defensive Distillation: This approach reduces the model’s sensitivity to adversarial perturbations by smoothing the decision boundaries, making it harder for subtle modifications to alter the AI’s output [55].
- Feature Squeezing: By reducing the complexity of input data, feature squeezing eliminates extraneous features that could be Techniques such as image bit depth reduction or smoothing can mitigate adversarial input by stripping away noise and focusing on essential information [56].
- Robustness Verification: Formal methods and automated testing frameworks can be applied to verify the resilience of AI models against adversarial perturbations, providing assurances that the models perform reliably under a range of potential attack scenarios [57].
8.2. Supply Chain Attacks
The complexity of AV supply chains introduces vulnerabilities that can be targeted through various means. Addressing these requires both organizational and technical strategies:
- Blockchain for Component Tracking: Implementing blockchain can provide transparent and immutable records for each component’s origin and journey through the supply chain, helping to ensure that only verified components are integrated into AV systems [58, 59].
- Secure Boot and Hardware Roots of Trust: Secure boot mechanisms ensure that AV systems only load authenticated software at Hardware roots of trust further protect the integrity of the system by establishing a secure hardware foundation, preventing malware insertion at the hardware level [58].
- Code Signing and Verification: All software updates and components should be cryptographically signed, and systems must verify these signatures before applying any updates. This process ensures that only authorized and untampered code is executed within AV systems.
- Comprehensive Vulnerability Assessments: Regular security audits and vulnerability assessments are essential for identifying and mitigating potential supply chain weaknesses. By partnering with trusted third- party cybersecurity firms, manufacturers can gain additional insights into their supply chain’s security posture [59].
8.3. Ransomware Attacks Targeting Vehicle Systems
Ransomware poses a growing threat to AV systems by potentially locking critical functionalities. Effective counter- measures include:
- Strong Encryption and Backup Protocols: Encrypting key data within the vehicle’s system and maintaining secure, regularly updated backups can prevent data loss and facilitate recovery in case of a ransomware attack [47].
- Endpoint Detection and Response (EDR): Advanced EDR systems provide real-time monitoring of AV end- points, detecting unusual patterns that may indicate ransomware activities. Rapid response capabilities enable the containment and neutralization of threats before they escalate.
- Anomaly Detection Systems: Employing machine learning models that analyze normal system behaviors can help detect ransomware When abnormal behavior patterns are identified, such as unauthorized encryption attempts, the system can isolate affected modules to prevent further damage [47].
8.4. Keyless Car Theft and Relay Attacks
AVs with keyless entry systems are susceptible to relay attacks that intercept and amplify signals between the key fob and the vehicle. Countermeasures include:
- Ultra-Wideband (UWB) Technology: UWB-based systems offer enhanced accuracy in determining the proximity of the key fob to the vehicle, reducing the likelihood of successful relay attacks [60].
- Two-Factor Authentication (2FA) for Access: By requiring a secondary authentication step (such as a smartphone verification) [61], AVs can add an additional layer of security that limits unauthorized
- Interference Detection Systems: These systems monitor and detect signal anomalies associated with relay attacks, enabling AVs to trigger alerts or disable keyless entry temporarily when an attack is suspected.
8.5. Risks in Autonomous Vehicle Charging Infrastructure
AV charging stations are potential targets for cyberattacks that could disrupt vehicle operations. Mitigating these risks involves:
- Transport Layer Security (TLS) Protocols: Secure communication between AVs and charging stations through TLS [62] ensures data integrity and confidentiality, making it more challenging for attackers to intercept or manipulate information.
- Network Segmentation and Firewalls: Isolating charging stations from broader vehicle and grid networks prevents unauthorized access and contains attacks to specific segments, limiting the scope of potential damage.
- Regular Cybersecurity Audits: Continuous monitoring and assessment of charging infrastructure cybersecurity are necessary to identify and mitigate emerging threats, ensuring robust defenses against attacks.
8.6. Countermeasures for Traffic Jams and Noise Pollution
Cybercriminals could exploit AV functionalities to create traffic disruptions and noise pollution. To counter these risks:
- Decentralized Control Protocols: Implementing decentralized control systems helps distribute vehicle decision-making, reducing susceptibility to coordinated attacks that could cause traffic jams.
- Honk Limiting Features and Scheduling: AVs can incorporate software that restricts honking based on the time of day and location, reducing potential disturbances in residential areas and mitigating risks if systems are compromised.
By implementing these strategies, the AV industry can establish a strong cybersecurity framework that safeguards vehicles against a variety of changing threats, thereby ensuring the safety and security of passengers and urban settings.
9. Statistical Analysis
9.1. The Status of Self-Driving Cars
In 2023, the development of autonomous vehicle (AV) technology is still ongoing, and there are currently only a limited number of self-driving cars being used on U.S. roads. Many of these vehicles are currently undergoing testing to assess and improve their self-driving capabilities. Last year, around 1,400 vehicles, including cars, trucks, and other types, were undergoing testing by 80 different companies in 36 states throughout the United States. In January 2023, Mercedes-Benz made history by becoming the first automaker in the U.S. to receive government approval for a Level 3 driving feature in Nevada [63]. This achievement marked a significant milestone in the automotive industry. Level 3 automation is of utmost importance as it signifies a remarkable leap forward from Level 2, enabling the vehicle to take care of all driving responsibilities while the driver only needs to step in when required. Despite the relatively small number of autonomous vehicles currently in use, the industry is witnessing significant expansion.
According to market analysis, the global autonomous vehicle (AV) market is expected to experience significant growth in the coming years. The market value is projected to increase from USD 1,921.1 billion in 2023 to USD 13,632.4 billion by 2030, with a compound annual growth rate (CAGR) of 32.3% during this period [64]. In 2022, the Asia-Pacific region emerged as the dominant player in the autonomous vehicle industry, capturing an impressive market share of 50.44%. According to these projections, the autonomous vehicle market is set to experience significant growth, fueled by advancements in technology and the growing acceptance of these vehicles in different regions.
9.2. Consumer Perception and Safety Concerns
Public trust and acceptance are pivotal to the widespread adoption of autonomous vehicles (AVs). While approximately 57% of Americans familiar with self-driving cars are willing to ride in them, and 55% believe that most vehicles will be autonomous by 2029, there remains a significant proportion of the population—43%—who express apprehension about using driverless vehicles [65]. Surveys indicate that safety concerns are at the core of this reluctance. For example, in 2024, AAA reported that about 66% of Americans harbor fears about fully autonomous vehicles due to incidents and perceived risks associated with these systems [66].
Additionally, a World Economic Forum report underscores the role of clear communication and regulatory transparency in enhancing public trust in AV technology. The report emphasizes that as people become more familiar with AV safety measures and technological advancements, their confidence is likely to grow, thereby facilitating a smoother transition to autonomous transportation systems [67]. Understanding and addressing these consumer concerns is crucial for real-world implementation, as public acceptance directly impacts adoption rates and can guide regulatory approaches to foster trust in AV technologies.
9.3. Automated Vehicle Accident Statistics
The safety of self-driving cars is a subject that sparks heated discussions, especially as the technology progresses. In 2022, automakers disclosed around 400 crashes to the National Highway Traffic Safety Administration (NHTSA) involving vehicles equipped with partially automated driver- assist systems. Out of all the incidents, 273 of them involved Tesla vehicles, and interestingly, 70% of these Teslas were using the Autopilot beta feature at the time. It is worth mentioning that 11 of the crashes reported led to severe injuries, while five of them tragically resulted in fatalities. Meanwhile, in 130 reported accidents involving fully autonomous vehicles, there were no injuries in 108 cases, with the majority of incidents being rear-end collisions [65].
9.4. Liability in Autonomous Vehicle Accidents
Assessing responsibility in accidents involving autonomous vehicles introduces an additional level of intricacy to conventional traffic incidents. When a self-driving car is involved in an accident, it becomes essential to determine if the automated driving system was active during the collision and the level of human driver intervention that was anticipated. If there is a suspicion of a flaw in the AV’s system, the incident might be subject to product liability law [68]. In such cases, it is necessary to provide evidence of the defect and establish a clear link between the defect and the resulting injury.
9.5. Market and Technological Advancements
The autonomous vehicle industry is making significant strides, with continuous advancements in levels of vehicle automation. Various systems currently exist, with different levels of assistance provided to drivers. At the lowest level, drivers receive only momentary assistance, while at the highest level, the vehicle is capable of handling all driving tasks in any condition. Driver-assist technologies have be- come a common feature in the majority of new cars. These technologies encompass a range of helpful features such as automatic emergency braking, lane-keeping assistance, and adaptive cruise control [69]. As companies like Mercedes- Benz receive approval to deploy these technologies, more advanced systems, such as Level 3 automation, are becoming increasingly prevalent. These systems allow vehicles to manage most driving tasks independently.
10. Comparative Analysis: Drones vs. Driverless Cars
Technological breakthroughs in autonomous systems have propelled drones and autonomous vehicles to the forefront of contemporary innovation, providing unparalleled advantages in transportation, logistics, and surveillance. Nevertheless, the autonomy that fuels these advantages also brings about substantial cybersecurity vulnerabilities, which give rise to concerns over their possible abuse.
Drones [70] and autonomous vehicles have common technological underpinnings, such as the utilization of GPS for navigation, sensors for environmental perception, and artificial intelligence (AI) for decision-making operations. Both technologies are highly dependent on real-time data processing and external connectivity, rendering them vulnerable to cyber attacks such GPS spoofing, jamming, and unauthorized data interception.
Nevertheless, their operational environments vary greatly. Drones function within airspace and are commonly employed for the purposes of surveillance, delivery, and reconnaissance, rendering them susceptible to abuse in illicit activities such as smuggling, covert surveillance, or even as weaponry [70]. Conversely, autonomous vehicles skillfully maneuver through intricate metropolitan landscapes, prioritizing transit and logistics, where the vulnerabilities to hacks encompass hijacking, remote control, and the potential for accidents. Understanding these potential threats is crucial for developing appropriate countermeasures.
Given these distinct yet overlapping vulnerabilities, it is essential to explore the specific ways in which both drones and AVs can be exploited by cybercriminals. The following subsections delve into these potential threats, comparing how they manifest in drones and AVs.
10.1. Tracking and Surveillance
Driverless cars can be misused as tools for tracking and surveillance. Since these vehicles are equipped with GPS, cameras, and other sensors, a compromised car can be used to monitor an individual’s movements without their knowledge. Cybercriminals or other malicious entities could hijack the car’s systems to gather real-time data about the location and activities of the occupants, effectively turning the vehicle into a surveillance tool. While drones are also susceptible to being used for surveillance, their typical use in airspace makes them less likely to be involved in long- term tracking within dense urban environments, where AVs are more commonly found. This kind of misuse raises significant privacy concerns, especially if sensitive personal information is intercepted or recorded.
10.2. Transporting Illegal Items
Driverless cars could be exploited for the unauthorized transportation of illegal goods, such as drugs, weapons, or contraband. Since these vehicles operate autonomously, they could be programmed to follow predetermined routes to specific drop-off locations, reducing the need for human involvement and lowering the risk of detection.
Drones, too, are vulnerable to such misuse, particularly for smuggling goods across borders or into restricted areas. However, the ground-based nature of AVs means they are more likely to be used for covert operations within urban areas. This capability could be particularly appealing to criminal organizations looking to minimize the risks associated with traditional methods of smuggling and transportation.
10.3. Weaponization and Terrorism
In the worst-case scenarios, driverless cars could be weaponized by cybercriminals or terrorists. By hijacking a vehicle’s control systems, an attacker could direct the car to drive into a crowded area or a critical piece of infrastructure, such as a bridge or a building. The vehicle could also be loaded with explosives or hazardous materials, turning it into a remote-controlled bomb. While drones have similarly been considered for such malicious purposes due to their aerial capabilities, the ground-based nature of autonomous vehicles allows them to carry larger payloads and target densely populated urban environments more effectively. The potential for such attacks highlights the importance of securing the software and communication systems of autonomous vehicles to prevent their use in acts of terrorism.
10.4. Coordinated Cyberattacks
Driverless cars, like drones, are part of a broader network of interconnected systems, including other vehicles, traffic management systems, and cloud-based services. This inter- connectivity increases the risk of coordinated cyberattacks [71], where multiple vehicles are compromised and used in concert to achieve a malicious goal. Such attacks could disrupt urban infrastructure, create widespread panic, or even be used as a tool for cyber warfare. The ability to remotely control large numbers of autonomous vehicles presents a unique challenge to cybersecurity professionals, who must develop strategies to detect and neutralize such threats before they can cause harm. For instance, the Ukrainian government has developed advanced drone systems capable of coordinated attacks [72]. These drones can intercommunicate, autonomously decide on targets, and collect intelligence at speeds surpassing human capabilities. This development illustrates the potential for autonomous systems to be used in coordinated actions, highlighting the need for robust cybersecurity measures in both military and civilian autonomous vehicle networks.
11. Societal Impacts
11.1. Transportation Accessibility
Driverless cars have the potential to significantly improve transportation accessibility for individuals with disabilities, the elderly, and those who cannot drive. Autonomous vehicles (AVs) can provide on-demand mobility services, enhancing independence and quality of life for these populations. For example, AVs could offer new mobility options to the approximately 49 million Americans over the age of 65 and the 53 million people with some type of disability. This increase in accessibility could result in a 14% rise in vehicle miles traveled, potentially worsening congestion but significantly improving individual mobility and independence [73]. Furthermore, automated vehicles could create new employment opportunities for about 2 million people with disabilities in the United States [74].
11.2. Urban Planning and Traffic Management
Autonomous vehicles are expected to have a profound impact on urban planning and traffic management. By reducing the need for extensive parking facilities and enabling more efficient use of road space, AVs can contribute to better urban environments. Improved traffic management through vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communication can reduce congestion and optimize traffic flow. Platooning, where vehicles travel closely together, can increase road capacity and reduce traffic delays [73]. Additionally, shared mobility services facilitated by AVs can support car-sharing concepts, reducing the number of privately owned vehicles and promoting more sustainable urban transport models [74].
11.3. Environmental Considerations
The adoption of electric autonomous vehicles can significantly contribute to environmental sustainability by reducing greenhouse gas emissions and improving air quality. Efficient driving patterns and reduced congestion lead to lower fuel consumption and environmental impact. According to the U.S. Chamber of Commerce, autonomous vehicles have the potential to prevent 1.4 million accidents and 12,000 fatalities annually, resulting in substantial economic savings of $94 billion [75]. Moreover, the shift towards shared autonomous vehicles can further reduce the overall number of vehicles on the road, decreasing the carbon footprint associated with manufacturing and operating personal vehicles.
11.4. Job Displacement and Economic Implications
The transition to driverless cars may lead to job displacement in industries such as trucking, taxi services, and public transportation. In the United States, approximately 2.9% of workers are employed in driving occupations, with more than 4 million potentially affected by the adoption of AVs. This could result in an estimated annual income loss of around $180 billion for these workers [73]. However, the rise of autonomous vehicles also presents opportunities for economic growth, including new jobs in technology development, infrastructure upgrades, and mobility services. The motor insurance industry, worth over $300 billion annually in the U.S., may also experience significant changes as AVs reduce the frequency and severity of accidents, potentially lowering insurance premiums for consumers [73].
12. Regulatory Landscape
12.1. Government Initiatives and Policies
Governments worldwide are actively developing initiatives and policies to support the deployment of autonomous vehicles (AVs). These efforts include funding for research and development, establishing testing and certification standards, and creating frameworks for AV integration into existing transportation systems. For instance, in the United States, the National Highway Traffic Safety Administration (NHTSA) continues to lead federal efforts, focusing on creating guidelines that ensure safety while promoting innovation. Various states are also pioneering regulatory efforts by passing laws and executive orders to facilitate AV testing and deployment, highlighting the importance of harmonized federal regulations to avoid a fragmented regulatory landscape.
12.2. Legal Framework for Autonomous Vehicles
Establishing a robust legal framework is essential for the safe and effective deployment of AVs. Key components of this framework include:
- Defining Liability: Clarifying liability in the event of accidents involving AVs is crucial. This involves determining the responsibility between manufacturers, software developers, and vehicle Some states, like California, Nevada, and Florida, have implemented requirements for manufacturers to hold significant insurance policies or bonds to cover potential damages.
- Setting Standards for Performance and Safety: Governments are establishing standards for vehicle performance and safety to ensure that AVs can operate safely on public These standards cover aspects such as sensor accuracy, fail-safe mechanisms, and emergency response capabilities.
- Ensuring Data Privacy Compliance: As AVs collect and process vast amounts of data, ensuring compliance with data privacy regulations is essential to protect user information and maintain public trust.
12.3. International Standards and Collaboration
International collaboration and the establishment of global standards are crucial for the interoperability and scalability of autonomous vehicle technology. Organizations such as the International Organization for Standardization (ISO) and SAE International play key roles in developing these standards. For example, the European Union has finalized a legal framework for fully automated vehicles, creating binding regulations that include comprehensive safety and performance criteria. Collaborative efforts are also evident in cross-border initiatives, where countries work together to create harmonized regulatory approaches, enabling seamless operation of AVs across different jurisdictions.
12.4. Comparative Regulatory Frameworks in Europe and Asia
European and Asian countries have developed distinctive regulatory frameworks that address the deployment and operation of AVs, reflecting diverse regional priorities and challenges. In the European Union (EU), regulations such as the General Safety Regulation mandate that all new vehicles include advanced driver assistance systems (ADAS) by 2022, encompassing features like lane-keeping and automated emergency braking. Furthermore, UN Regulation 157 on Automated Lane Keeping Systems (ALKS) permits Level 3 AVs on public roads, provided they meet strict safety, cybersecurity, and software update requirements. Germany, a leader within the EU, enacted a law in 2021 allowing Level 4 AVs to operate in specified public areas, setting a precedent for comprehensive AV legislation [76].
In the United Kingdom, efforts to position itself as an AV innovation hub are underscored by significant investments exceeding £200 million in AV testing and research infrastructure. The UK’s Code of Practice for Testing Automated Vehicles provides guidelines on liability, insurance, and data protection, facilitating AV trials on public roads. By 2025, the UK aims to establish a legal framework to support widespread AV deployment, focusing on safety standards and clarifying manufacturer and user responsibilities [77].
In Asia, Japan has prioritized AV integration into public transport, especially in rural areas, and revised the Road Transport Vehicle Law to permit Level 3 AVs on public roads. Japan is actively preparing for the 2025 World Expo in Osaka, where Level 4 AVs are expected to be deployed [78]. China, another major player, has developed city-specific policies, allowing for Level 4 testing in cities like Beijing and Shanghai. The Beijing Autonomous Driving Policy includes data security requirements, emphasizing compliance with national laws like the Cybersecurity Law and the Personal Information Protection Law (PIPL) [79]. South Korea, aspiring to be an AV industry leader, has implemented the Framework Act on Intelligent Robots to regulate AVs, along with establishing K-City, a large-scale AV testing facility simulating urban and highway environments [80].
13. Results
In this section, the primary findings of the study are presented, with a particular emphasis on the comparative analysis of cybersecurity threats facing autonomous vehicles (AVs) and drones. By examining the common vulnerabilities between these two technologies, this research sheds light on potential threats that AVs may encounter, drawing parallels from the established cybersecurity issues in drone systems. This cross-technology perspective provides valuable insights into emerging risks and underscores the importance of proactive threat mitigation.
Additionally, a comparison with recent related works is included to underscore the unique contributions of this study. Table 2 summarizes how this research diverges from existing literature by specifically focusing on emerging and future cybersecurity threats in AVs, inferred from drone vulnerabilities. This approach offers a forward-looking view on cybersecurity challenges, providing a foundation for understanding and anticipating potential misuse of AV technology.
Table 2: Threats in Autonomous Vehicles with Status
Threat | Potential Impact on AVs | Status |
Remote Exploits | Unauthorized control over AV functions, posing safety risks | Existing |
GPS Spoofing | Misleading AV navigation, causing route deviations | Emerging |
Adversarial ML Attacks | Misinterpretation of road signs or obstacles, leading to unsafe decisions | Emerging |
Supply Chain At- tacks | Risk of tampered AV components before deployment | Emerging |
Ransomware | Potential to incapacitate AV systems until payment is made | Possible Future |
Denial of Service (DoS) | System overload, disrupting AV operations and real-time data processing | Possible Future |
Noise Pollution | Excessive AV honking and increased vehicle numbers could heighten urban noise levels | Possible Future |
Traffic Conges- tion | More AVs on roads could worsen traffic if not managed effectively | Possible Future |
Risks in AV Charging Infras- tructure and | Cyberattacks on charging stations, grid strain, and bottlenecks at charging sites | Possible Future |
Tracking Surveillance | Unauthorized tracking using AVs for long- term monitoring within urban areas | Emerging |
Transporting Ille- gal Items | Use of AVs for transporting contraband au- tonomously within urban settings | Possible Future |
Weaponization and Terrorism | Hijacking AVs for attacks or as remote- controlled bombs targeting urban areas | Possible Future |
Coordinated Cy- berattack | Large-scale attacks involving multiple AVs to disrupt traffic or emergency response systems | Possible Future |
14. Limitations
While this paper offers a broad survey of autonomous vehicle (AV) technology, it is limited by its high-level perspective, which does not delve into specific implementation details. The generalized nature of this study may not fully reflect the unique technological approaches of different manufacturers, thereby limiting the applicability of its find- ings across various AV systems. Additionally, due to the rapid pace of advancements in AV technology, some insights presented here may quickly become outdated as new innovations in sensors, AI algorithms, and cybersecurity measures continue to evolve.
Furthermore, the study focuses mainly on technological and cybersecurity challenges, with less emphasis on the ethical and social implications of AV adoption. Complex issues, such as the potential impact on employment, ethical considerations in AI-driven decision-making, and regional differences in regulatory readiness, are acknowledged but not explored in depth. Future research could address these areas by conducting case studies, longitudinal analyses, and interdisciplinary investigations that incorporate ethical, social, and regional dimensions, providing a more holistic view of the challenges and opportunities surrounding autonomous vehicles.
15. Conclusion
Autonomous vehicles (AVs) signify a profound paradigm shift within the transportation sector, bearing both theoretical and practical ramifications. From a theoretical standpoint, AVs provide insights into the interplay of artificial intelligence, sensor integration, and real-time decision-making within complex systems. On a practical level, they present promising strategies to enhance road safety, alleviate traffic congestion, and mitigate the environmental consequences associated with conventional transportation. This study illustrates how the convergence of advanced sensors, AI al- gorithms, and vehicle-to-everything (V2X) communication technologies is advancing the AV landscape.
A key contribution of this research is the delineation of essential technologies and the examination of cyberse- curity challenges that AVs encounter. By analyzing these elements, this study highlights the imperative need for ro- bust cybersecurity frameworks designed to safeguard AV systems against potential threats. Furthermore, the study underscores the necessity for comprehensive regulatory frameworks that can foster public trust and support the widespread adoption of AV technology.
From an applied perspective, AVs are poised to deliver numerous benefits. They hold the potential to drastically reduce road fatalities attributable to human error, which remains a leading cause of vehicular accidents worldwide. In addition, AVs can enhance traffic management by optimizing routing and facilitating communication between vehicles and infrastructure, thereby promoting more efficient road usage. Moreover, the shift towards electric AVs offers considerable potential for reducing greenhouse gas emissions and supporting broader environmental sustainability goals. Nevertheless, this research acknowledges certain limitations. Although it provides a comprehensive overview of AV technology and its associated challenges, the study does not delve into the specific implementation variations across different AV manufacturers. Additionally, given the rapid pace of technological advancements in this domain, the findings presented are susceptible to obsolescence. Future research could address these limitations by conducting longitudinal studies to track the ongoing evolution of AV technologies.
Looking forward, several avenues for future research merit attention. First, there is a pressing need for the development of standardized cybersecurity protocols that address the specific challenges posed by real-time data exchange and autonomous decision-making in AVs. Second, further research should explore the socio-economic impacts of AV proliferation, particularly concerning potential job displacement within the driving sector. Finally, interdisciplinary studies that integrate perspectives from urban planning, ethics, and AI safety are essential to comprehensively understand how AVs will reshape transportation infrastructure and societal frameworks.
In conclusion, autonomous vehicles offer a transforma- tive opportunity to develop transportation systems that are safer, more efficient, and more sustainable. Addressing the current challenges will necessitate ongoing collaboration among policymakers, industry stakeholders, and the research community. By surmounting these obstacles, AVs have the potential to become a fully integrated aspect of modern society, fundamentally altering the way we navigate our world for generations to come.
- T. Kanade, C. Thorpe, W. Whittaker, “Autonomous land vehicle project at cmu”, “Proceedings of the 1986 ACM Fourteenth Annual Conference on Computer Science”, CSC ’86, pp. 71–80, ACM, New York, NY, USA, 1986, doi:10.1145/319838.319850.
- Mobileeye, “History of autonomous vehicles: From renaissance to reality”, https://shorturl.at/asq4I, 2023, accessed: 2024-07-05.
- Arrow, “History of self-driving cars”, https:// www.arrow.com/en/research-and-events/articles/
the-history-of-self-driving-cars, accessed: 2024-07-05. - S. Magazine, “The national automated highway system that almost was”, https://shorturl.at/UbL7x, 2013, accessed: 2024-07-05.
- Google, “Waymo: On the road”, https://waymo.com/ontheroad/, 2017, accessed: 2024-07-05.
- G. V. Research, “Autonomous vehicle market to reach
$214.32bn by 2030”, https://www.grandviewresearch.com/ industry-analysis/autonomous-vehicle-market, 2023, accessed:
2024-07-05. - McKinsey and Company, “Autonomous vehicles moving forward: Perspectives from industry leaders”, 2024, article.
- K. Bian, G. Zhang, L. Song, “Security in use cases of vehicle-to-everything communications”, “2017 IEEE 86th Ve- hicular Technology Conference (VTC-Fall)”, pp. 1–5, 2017, doi:10.1109/VTCFall.2017.8288208.
- F. B. Insights, “Autonomous vehicle market size, share, trends report [2030]”, https://www.fortunebusinessinsights.com/ autonomous-vehicle-market-102020, 2023, accessed: 2024-07-05.
- P. Research, “Autonomous vehicle market size to hit usd 2,752.80 bn by 2033”, https://www.precedenceresearch.com/ autonomous-vehicle-market, 2023, accessed: 2024-07-05.
- Precedence Research, “Autonomous vehicle market size to hit usd 2,752.80 bn by 2033”, https://www.precedenceresearch. com/autonomous-vehicle-market#:~:text=The%20global% 20autonomous%20vehicle%20market,USD%2059.92%20billion% 20in%202023, 2024, last updated: June 2024.
- W. H. Organization, “Global status report on road safety 2018”, World Health Organization, 2018, accessed: 2024-07-05.
- WHO, “Global status report on road safety 2023”, World Health Orga- nization, 2023, accessed: 2024-07-05.
- W. H. Organization, “Road traffic injuries”, World Health Organization, 2023, accessed: 2024-07-05.
- Spectrum, “Autonomous vehicles can make all cars more efficient”, https://shorturl.at/9ht7y, 2018, accessed: 2024-07-05.
- McKinsey, Company, “The future of au- tonomous vehicles (av)”, https://www.mckinsey.com/ industries/automotive-and-assembly/our-insights/ the-future-of-autonomous-vehicles-av, 2023, accessed: 2024-07- 05.
- ScienceDirect, “The impacts of connected autonomous vehicles on mixed traffic flow: A review”, https://www.sciencedirect.com/ science/article/pii/S2352146520305170, 2020, accessed: 2024- 07-05.
- N. Geographic, “Energy implications of autonomous vehicles: Imagining the possibilities”, https:// www.nationalgeographic.com/environment/article/
energy-implications-of-autonomous-vehicles, 2019, accessed: 2024-07-05. - B. C. Group, “Can self-driving cars stop the urban mobility melt- down?”, https://shorturl.at/F0d5d, 2020, accessed: 2024-07-05.
- R. Du, et al., “Effective urban traffic monitoring by vehicular sensor networks”, IEEE Transactions on Vehicular Technology, vol. 64, no. 1, pp. 273–286, 2014, doi:10.1109/TVT.2014.2349320.
- Y. Li, et al., “Vehicle detection based on the and–or graph for congested traffic conditions”, IEEE Transactions on Intelligent Transportation Sys- tems, vol. 14, no. 2, pp. 984–993, 2018, doi:10.1109/TITS.2018.2871040.
- R. F. Foundation, “Self-driving cars: The impact on people with disabilities”, Ruderman White Paper, 2017.
- R. Corporation, “Self-driving vehicles offer potential benefits, policy challenges for lawmakers”, RAND Corp, 2014.
- N. C. Onat, J. Mandouri, M. Kucukvar, et al., “Rebound effects undermine carbon footprint reduction potential of autonomous electric vehicles”, Nature Communications, vol. 14, p. 6258, 2023, doi:10.1038/s41467-023-41992-2, received 01 May 2023, Accepted 22 September 2023, Published 06 October 2023.
- A. J. G. Rodríguez, N. J. Barón, J. M. G. Martínez, “Validity of dynamic capabilities in the operation based on new sustainability narratives on nature tourism smes and clusters”, Sustainability, vol. 12, no. 3, p. 1004, 2020, doi:10.3390/su12031004.
- Y. Zhang, Z. Wang, H. Wang, F. Blaabjerg, “Artificial intelligence- aided thermal model considering cross-coupling effects”, IEEE Trans- actions on Power Electronics, vol. 35, no. 10, pp. 9998–10002, 2020, doi:10.1109/TPEL.2020.2980240.
- KPMG, “Connected and autonomous vehicles – readiness index”, https://t.ly/_tAW_, 2020, accessed: 2024-07-05.
- SMMT, “Connected and autonomous vehicles: The global race to mar- ket”, https://tinyurl.com/4kdakunk, 2021, accessed: 2024-07-05.
- R. Domínguez, E. Onieva, J. Alonso, J. Villagra, C. González, “Lidar based perception solution for autonomous vehicles”, “Intelligent Systems Design and Applications (ISDA), 2011 11th International Conference on”, pp. 790–795, 2011.
- E. Hasch, R. Topak, R. Schnabel, T. Zwick, R. Weigel, C. Wald- schmidt, “Millimeter-wave technology for automotive radar sen- sors in the 77 ghz frequency band”, IEEE Transactions on Mi- crowave Theory and Techniques, vol. 60, no. 3, pp. 845–860, 2012, doi:10.1109/TMTT.2011.2178427.
- M.-H. Lee, Y.-J. Chen, T. Li, “Sensor fusion design for navigation and control of an autonomous vehicle”, “2011 IEEE International Conference on Systems, Man, and Cybernetics (SMC)”, pp. 2209–2214, 2011, doi:10.1109/ICSMC.2011.6084000.
- Q. Li, L. Chen, M. Li, S.-L. Shaw, A. Nuchter, “A sensor-fusion drivable- region and lane-detection system for autonomous vehicle navigation in challenging road scenarios”, IEEE Transactions on Vehicular Technol- ogy, vol. 63, no. 2, pp. 540–555, 2014, doi:10.1109/TVT.2013.2289913.
- B. Padmaja, C. Moorthy, N. Venkateswarulu, et al., “Exploration of issues, challenges and latest developments in autonomous cars”, Jour- nal of Big Data, vol. 10, no. 61, 2023, doi:10.1186/s40537-023-00701-y, published: 06 May 2023.
- L. Hobert, A. Festag, I. Llatser, L. Altomare, F. Visintainer, A. Kovacs, “Enhancements of v2x communication in support of cooperative au- tonomous driving”, IEEE Communications Magazine, vol. 53, pp. 64–70, 2015, doi:10.1109/MCOM.2015.7105641.
- S. A. Centers, “The six levels of autonomous driving”, https://www.schaeferautobody.com/ the-six-levels-of-autonomous-driving/#:~:text= Conditional%20Automation%20(Level%203)%20Vehicles% 20at%20this,to%20monitor%20for%20changes%20in%20those% 20conditions, 2019, accessed: October 11, 2024.
- A. Greenberg, “Hackers remotely kill a jeep on the high- way—with me in it”, https://www.wired.com/2015/07/ hackers-remotely-kill-jeep-highway/, 2015, accessed: 2024-08- 26.
- The Guardian, “Uber’s joe sullivan faces trial over data breach cover- up”, The Guardian, 2022, accessed: 2024-08-30.
- H. Shin, D. Won, S. Kim, “Gps spoofing attack on autonomous vehicles and its countermeasure”, IEEE Transactions on Intelli- gent Transportation Systems, vol. 20, no. 5, pp. 1738–1748, 2019, doi:10.1109/TITS.2019.2896358.
- J. Kenney, “Jamming attack vulnerabilities in v2x communication systems”, “IEEE Vehicular Technology Conference (VTC2021-Fall)”, 2021, doi:10.1109/VTCFall2021.2019.9198881.
- A. Hamid, P. Lin, R. Hussain, “Relay attacks in vehicular networks: Analysis, impact, and solutions”, IEEE Communications Magazine, vol. 60, no. 4, pp. 79–85, 2022, doi:10.1109/MCOM.2022.3056782.
- Q. Yan, D. Zhang, “Sensor spoofing attacks on autonomous vehicles: A review of the vulnerabilities and mitigation strategies”, IEEE Com- munications Surveys & Tutorials, vol. 22, no. 4, pp. 2835–2856, 2020, doi:10.1109/COMST.2020.2976336
- I. Foster, K. Koscher, “Tesla model s: A case study in software security and over-the-air updates”, Journal of Cybersecurity, vol. 6, no. 1, pp. 1–15, 2018, doi:10.1093/cybsec/tyy010.
- J. Petit, S. Shladover, “Mitm attacks on connected vehicles: Techniques, impact, and countermeasures”, IEEE Vehicular Technology Magazine, vol. 15, no. 2, pp. 70–77, 2020, doi:10.1109/MVT.2020.2983621.
- M. Groll, S. R. Weller, “Denial-of-service attacks in autonomous vehicle networks: A comprehensive analysis”, IEEE Transac- tions on Intelligent Vehicles, vol. 4, no. 3, pp. 400–412, 2019, doi:10.1109/TIV.2019.2937765.
- T. B. Brown, D. Mane, A. Roy, M. Abadi, J. Gilmer, “Adversarial patch”, https://arxiv.org/abs/1907.07736, 2019, accessed: 2024-08-26.
- U.S. News and World Report, “Car dealerships are being disrupted by a multi-day outage after cyberattacks on software supplier”, https://shorturl.at/1bgnQ, 2024, accessed: 2024-08-30.
- S. C. Nayak, V. Tiwari, B. K. Samanthula, “Review of ransomware attacks and a data recovery framework using autopsy digital foren- sics platform”, “2023 IEEE 13th Annual Computing and Commu- nication Workshop and Conference (CCWC)”, pp. 0605–0611, 2023, doi:10.1109/CCWC57344.2023.10099169.
- L. Eliot, “Here’s how ransomware is going to fiendishly impede ai self-driving cars”, https://shorturl.at/ptDMH, 2021, accessed: 2024-08-30.
- Nahla Davies, “Keyless car theft”, https://shorturl.at/d5PLL, 2023, accessed: 2024-08-30.
- Alan J, “Bluetooth relay attacks”, https://thecyberexpress.com/ tesla-ultra-wideband-vulnerable-relay-attacks/, 2024, ac- cessed: 2024-08-30.
- David Strom, “Ev charging stations still riddled with cybersecu- rity vulnerabilities”, https://shorturl.at/vpv6y, 2024, accessed: 2024-08-30.
- Chris Isidore, “Driverless cars flood san francisco: What happens when things go wrong?”, https://www.cnn.com/2023/08/14/ business/driverless-cars-san-francisco cruise/index.html, 2023, accessed: 2024-08-30.
- J. Marcus, “San francisco residents fed up with self-driving car honk- ing”, https://shorturl.at/zQT5p, 2024, accessed: 2024-10-10.
- I. J. Goodfellow, J. Shlens, C. Szegedy, “Explaining and harnessing adversarial examples”, arXiv preprint arXiv:1412.6572, 2015, adver- sarial training improves model robustness by training AI models on adversarial examples.
- N. Papernot, P. McDaniel, X. Wu, S. Jha, A. Swami, “Distillation as a defense to adversarial perturbations against deep neural networks”, IEEE Symposium on Security and Privacy, 2016, defensive distillation smooths decision boundaries to mitigate the impact of adversarial inputs.
- W. Xu, D. Evans, Y. Qi, “Feature squeezing: Detecting adversarial examples in deep neural networks”, arXiv preprint arXiv:1704.01155, 2018, feature squeezing reduces input complexity to counter adver- sarial attacks.
- X. Huang, M. Kwiatkowska, S. Wang, M. Wu, “Safety verification of deep neural networks”, arXiv preprint arXiv:1610.06940, 2017, robust- ness verification through formal methods ensures AI model resilience against adversarial perturbations.
- IEEE Smart Cities, “Secure boot and hardware roots of trust in autonomous vehicles”, https://smartcities.ieee.org/security/ autonomous-vehicle-security, 2023, accessed: 2023-10-11.
- IBM – United States, “Ibm blockchain technology”, https://www.ibm. com/blockchain/supply-chain, 2023, accessed: 2023-10-11.
- Y. Rahayu, T. A. Rahman, R. Ngah, P. Hall, “Ultra wideband technol- ogy and its applications”, “2008 5th IFIP International Conference on Wireless and Optical Communications Networks (WOCN ’08)”, pp. 1–5, 2008, doi:10.1109/WOCN.2008.4542537.
- S. Ibrokhimov, K. L. Hui, A. Abdulhakim Al-Absi, h. j. lee, M. Sain, “Multi-factor authentication in cyber physical system: A state of art survey”, “2019 21st International Conference on Ad- vanced Communication Technology (ICACT)”, pp. 279–284, 2019, doi:10.23919/ICACT.2019.8701960.
- D. Zelle, C. Krauß, H. Strauß, K. Schmidt, “On using tls to se- cure in-vehicle networks”, “Proceedings of the 12th International Conference on Availability, Reliability and Security”, ARES ’17, As- sociation for Computing Machinery, New York, NY, USA, 2017, doi:10.1145/3098954.31058.
- Mercedes-Benz Group, “Drive pilot: Nevada becomes first us state to approve sae level 3 system for mercedes-benz”, https: //group.mercedes-benz.com/innovation/product-innovation/ autonomous-driving/drive-pilot-nevada.html, 2024, accessed: 2024-08-30.
- Fortune Business Insights, “Autonomous vehicle market size, share and covid-19 impact analysis, by component (hardware and soft- ware), by type (passenger car and commercial vehicle), and regional forecast, 2023-2030”, https://www.fortunebusinessinsights.com/ autonomous-vehicle-market-109045, 2024, accessed: 2024-08-30.
- KNR Legal, “Self-driving car accident statistics”, https://www.knrlegal.com/car-accident-lawyer/ self-driving-car-accident-statistics/, 2024, accessed: 2024-08-30.
- AAA, “2024 aaa survey on autonomous vehicles”, https://newsroom. aaa.com/2024/05/aaa-survey-autonomous-vehicles/, 2024, ac- cessed: 2024-10-10.
- W. E. Forum, “Which trends are driving the autonomous vehicles industry?”, https://www.weforum.org, accessed: 2024-07-05.
- Byrd Davis Alden and Henrichson, LLP, “Who is liable when a self-driving car causes a crash?”, https://shorturl.at/yZ7nY, 2024, accessed: 2024-08-30.
- Alliance for Automotive Innovation, “Autonomous vehicles”, https://www.autosinnovate.org/initiatives/innovation/ autonomous-vehicles, 2024, accessed: 2024-08-30.
- S. C. Nayak, B. K. Samanthula, V. Tiwari, “Investigating drone data recovery beyond the obvious using digital forensics”, “2023 IEEE 14th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON)”, pp. 0254–0260, 2023, doi:10.1109/UEMCON59035.2023.10315995.
- Cybersecurity and Infrastructure Security Agency (CISA), “Action guide for cybersecurity: Critical control actions”, https://www.cisa.gov/sites/default/files/2022-11/Action% 20Guide%20CCA%20508%20FINAL%2020190905.pdf, 2022, accessed: 2024-08-30.
- Kyiv Post, “Ukraine’s tech hub develops ai-driven drone swarms to combat russian forces”, https://www.kyivpost.com/post/34777, 2024, accessed:2024-08-30.
- F. Klaver, “The economic and social impacts of fully autonomous vehicles”, https://www.compact.nl, 2021, accessed: 2024-07-05.
- Bosch, “Impact of self-driving cars on society”, https://www.bosch. com, accessed: 2024-07-05.
- U. Chamber, “New u.s. chamber report on economic and social bene- fits of autonomous vehicles”, https://www.uschamber.com, accessed: 2024-07-05.
- European Commission, “Commission adopts new rules to support safe deployment of automated and connected vehi- cles in the eu”, https://ec.europa.eu/commission/presscorner/ detail/en/ip_22_4312, 2022, accessed: 2023-10-11.
- United Nations Economic Commission for Europe (UNECE), “Un regulation on automated lane keeping systems (alks) ex- tended to trucks, buses and coaches”, https://unece.org/ automated-lane-keeping-system-alks, 2021, https://unece. org/automated-lane-keeping-system-alks.
- Japan Times, “Kishida administration to boost self-driving car devel- opment in japan”, https://www.japantimes.co.jp/news/2024/08/ 01/japan/kishida-self-driving-cars-boost/, 2024, accessed: 2023-10-11.
- T. Staff Reporter, W. Ke, “China accelerates autonomous driving via multiple pilot cities, with beijing, shanghai, wuhan leading the charge”, https://t.ly/sMNut, 2024, accessed: 2023-10-11.
- Applied Intuition, “How the korean police science institute uses simian and basis to validate av stack performance”, https://www. appliedintuition.com/news/korea-police-science-institute, 2023, accessed: 2023-10-11.
