Histogram Based Visible Image Encryption for Real Time Applications
by Kiran 1,* ![]()
![]() , Sunil Kumar D S 2
, Sunil Kumar D S 2 ![]() , Bharath K N 3, Harshitha Rohith 4, Sharath Kumar A J 1
, Bharath K N 3, Harshitha Rohith 4, Sharath Kumar A J 1 ![]() , Ganesh Kumar M T 4
, Ganesh Kumar M T 4
1 Department of ECE, Vidyavardhaka College of Engineering, Mysuru, Karnataka, India
2 Department of Computer Science, Mangalore University, Mangalore, India
3 Department of ECE, DSATM, Bangalore, India
4 Department of ECE, G Madegowda Institute of Technology, Bharathinagara, Mandya Karnataka, India
* Author to whom correspondence should be addressed.
Journal of Engineering Research and Sciences, Volume 1, Issue 7, Page # 1-6, 2022; DOI: 10.55708/js0107001
Keywords: Region of interest, Medical Images, Encryption, Histogram, Peak Detection
Received: 18 February 2022, Revised: 11 June 2022, Accepted: 26 June 2022, Published Online: 18 July 2022
APA Style
Kiran, K., S, S. K. D., N, B. K., Rohith, H., J, S. K. A., & T, G. K. M. (2022). Histogram Based Visible Image Encryption for Real Time Applications. Journal of Engineering Research and Sciences, 1(7), 1–6. https://doi.org/10.55708/js0107001
Chicago/Turabian Style
Kiran, Kiran, Sunil Kumar D S, Bharath K N, Harshitha Rohith, Sharath Kumar A J, and Ganesh Kumar M T. “Histogram Based Visible Image Encryption for Real Time Applications.” Journal of Engineering Research and Sciences 1, no. 7 (July 1, 2022): 1–6. https://doi.org/10.55708/js0107001.
IEEE Style
K. Kiran, S. K. D. S, B. K. N, H. Rohith, S. K. A. J, and G. K. M. T, “Histogram Based Visible Image Encryption for Real Time Applications,” Journal of Engineering Research and Sciences, vol. 1, no. 7, pp. 1–6, Jul. 2022, doi: 10.55708/js0107001.
Like most patient information, medical imaging data is subject to strict data protection and confidentiality requirements. This raises the issue of sending the data which contains a medical image on an open network as per the above issue, also there might be a leakage of information. Encrypting an Image and hiding the information in it is the Potential way of avoiding this problem. But there might be many problems when we try restoring the original image. As a solution to that, an algorithm dealing with region of intrest (ROI) in medical images based on the pixels of interest and histogram peak technique. Firstly Image histogram peak technique is used for calculating peaks in medical images. Then set the Threshold value to segregate the pixels of interest in the medical images. The threshold value can be calculated by taking an average of all peaks in the histogram. These pixels are encrypted with the help of the Sudoku matrix. The proposed scheme will be evaluated using a various test based on statistics along with those results which will be compared to benchmarks of the existing work. We can see the better performance in terms of security from the proposed technique.
1. Introduction
Medical imaging research has made remarkable progress as a result of increased and improved investment in multimedia technology. The medical image contains the patient’s important personal privacy information. Medical images are usually encrypted to protect sensitive content. Common methods used for encrypting are International Data Encryption Algorithm, Data Encryption Standard to protect text data is commonly used [1]. We can see the distribution of pixels is uneven in data of Medical image with good resolution and various features. Regular cryptography used for image protection is not perfect to protect images from digital imaging and communication (DICOM) in medical care because of its inefficiency to handle huge data.
Observing the existing literature, the main issues of telemedicine are as follows. Traditional environments and cryptographic systems are:
- Secure medical images without loss of quality
- Maintain the reliability of confidential medical imaging data.
The aim of the proposed work includes three elements for the rapid and safe transmission of medical images.
- Confidentiality of Medical Images
- Integrity of Areas of Interest of medical images
- Safe recovery of images for diagnosis
The rest of the sections are as follows. Section 2 explained about various methods related to medical image encryption. Section 3 explains the basic concept of Sudoku used in the proposed encryption method. Section 4 explains the proposed work. Section 5 gives the performance analysis and finally, section 6 gives the conclusion of the work.
2. Related Works
In [2] authors proposed medical imaging is an effective and essential secondary information source they look into when a patient is to be diagnosed by a medical person. The faster way to share medical images is usually through an open network like email or file sharing. These methods will lead to copyright problems, illegal copy, and manipulation of the content. In [3] authors explained into medical image security focused on image encryption and information hiding has grown. In [4] authors explained a simple but efficient method by using matrix multiplication to change the value of a pixel in an image, which made the algorithm very simple but also made it very difficult for intruders to extract the information in the images. In [5] authors described abut 5-D hyperchaotic map actually the result of combining a logistic map with 3D Lorenz, which exhibited dual operating modes. One of the modes focuses only on the pixels obtained from clear text images while the other mode performs diffusion twice in order to obtain secured images. In [6] authors addressed the security issue made the confidential data from the web users be shared on web applications without fear and hence preserving their privacy. In [7] authors explained the improved chaotic map to obtain more security by identifying its drawbacks, followed by the introduction of a modified version of chosen plain text attack. In [8] authors described how to select the most important part of a medical image to hide confidential data. In [9] authors came up with partial encryption of images with secret data in images using FF3-1 and FF1. Without varying the size of the data, encryption of confidential data is done to reduce the usage of storage. In [10] authors introduce the grayscale encryption technique based on ROI with chaos. Using the Edge detection technique (Sobel), extraction of the ROI part is done. Lorenz’s system encrypts the sine map and ROI part which are required for the encryption. In [11] authors present a self-generating region of interest (ROI) method for watermarking application in biomedical images. This technique is robust enough to prevent many attacks such as Gaussian, median, sharpening, and wiener filters, which is the major advantage over other methods. In [12] authors discussed a new method to recover the information lossless from encryption in the transform domain. In [13, 14, 15, 16] authors come across a novel lossless game theory-based medical image encryption scheme with optimized ROI parameters along with ROI hidden positions. In [17] authors propose an HS method to examine the hidden lossless data in high-resolution medical images. Use high correlation for the smooth surface of medical imaging anatomy in the local block pixels of the image. In [18, 19] authors described about histogram peak detection of image is a fundamental technique for digital image processing that can be used directly and effectively for image segmentation, quality assessment, enhancement, and data reduction. In [20, 21, 22, 23] authors proposed the conventional indirect method to derive peak values. It consists of two steps. The first step is to fit the data to obtain a P D F. The second step is to calculate the derivative of the PDF to obtain significant peaks.
3. Sudoku Matrix
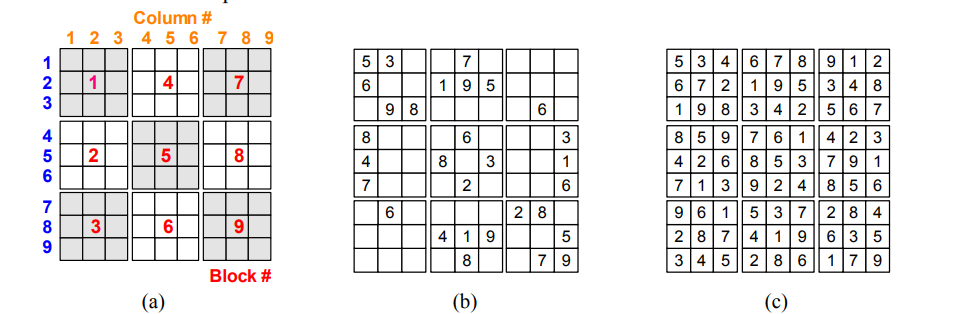
Here we define a Sudoku matrix as an X * X matrix containing numbers from 1 to N, but since X is the square of the number and N = X, each number occurs only once in each row. Increase only once in each column, only once in each block. Figure 1 below shows an example of a Sudoku puzzle and a solution for X = 9. The solution to the Sudoku puzzle is called the Sudoku matrix [24].
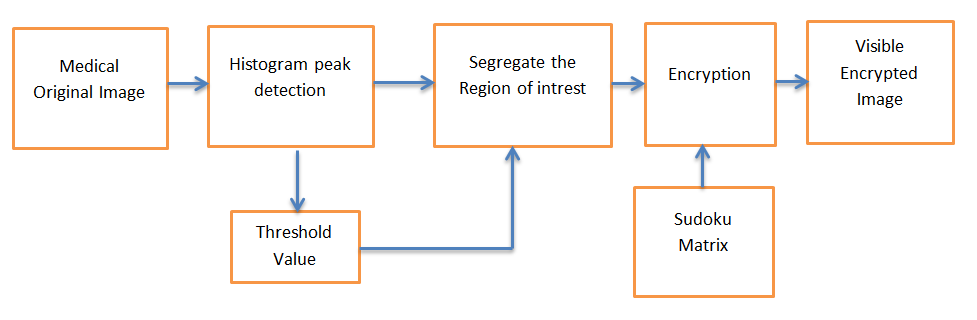
4. Proposed Visible Encryption Work
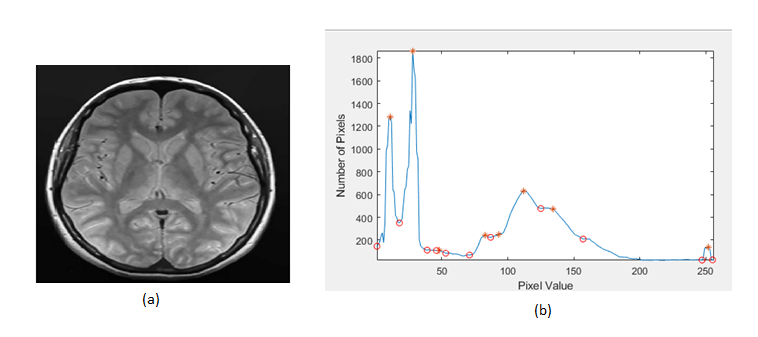
Block diagram of proposed selective image encryption system as shown in figure 2. The proposed system includes different steps for selecting and encoding regions of interest in medical images. First, calculate the histogram peak of the original medical image using the peak detection technique and as shown in Figure 3. The peak detection algorithm first generates a peak detection signal from the image histogram. The peaks in the histogram are then determined using the extreme point between the zero and zero intercepts of the peak detection signal. Convolution uses the first derivative approximation discriminator. For an ideal smooth histogram, the peak can be determined from the sign and zero intersection of the signal obtained from the h and S convolutions. The zero intersection estimates the extreme points of the histogram and the position of the turning point. The `*` symbol in figure 3 indicates the maximum values of the original medical image. The threshold value for separating the important pixels of the medical image can be calculated by taking the average of all the peak values obtained when the histogram peak is detected. Then compare each pixel of the original medical image with the threshold value, and if it is above the threshold value, group them into meaningful blocks of pixels. Sudoku matrix of multiples of 16*16 randomly generated for diffusion operation. Using pixels in a sudoku matrix, randomly encrypt a block of important pixels by performing an XOR operation.
Algorithm for encryption process:
- Step 1: Load the original medical image of size p*q.
- Step 2: Determine the histogram of original medical image.
- Step 3: Apply the histogram peak detection technique to extract all the possible peaks in the input image histogram.
- Step 4: Calculate the threshold value by averaging all the obtained peaks values.
- Step 5: Compare the every pixels in the original medical image with threshold value. If it is greater, then store the pixel into significant block.
- Step 6: Construct the Sudoku matrix with a same size of significant block.
- Step 7: Finally visible encrypted image is produced by performing XOR operation between significant block pixels and random pixels in the sudoku matrix.
5. Results and Discussion
The proposed technique is analyzed by evaluating the various parameters. Below are the parameters involved in this.
5.1. Analysis of Entropy
The amount of randomness is evaluated by Entropy in a cryptographic system. Equation of Entropy is [25-26]:
$$H(S) = \sum_{i=0}^{2^M – 1} P(s_i) \log_2 \left( \frac{1}{P(s_i)} \right) \tag{1}$$
where P (si) gives the probability of ith gray-level occurring in the image. Ideal entropy value for a random image is 8. If it is low, it is more predictable. Table 2 gives sample image’s entropy along with its respective cryptographic image.
5.2. M S E (Mean Square Error)
M S E is generally analyzed by averaging the squares of the difference between scrambled and plain scrambled image. Higher the value of M S E, the higher the encryption and the more noisy the clear image. The formula for MSE [27] given by.
$$MSE = \frac{1}{MN} \sum_{i=1}^{M} \sum_{j=1}^{N} \left[ inp(i,j) – enc(i,j) \right]^2
\tag{2}$$
5.3. P S N R(Peak Signal to Noise Ratio)
PSNR is always the reciprocal of the mean squared error (M S E). Increase MSE and reduce PSNR for better image security. Mathematically, the PSNR is given as follows [28].
$$PSNR = 10 \log_{10} \left( \frac{255^2}{MSE} \right)\tag{3}$$
5.4. UACI and NPCR
NPCR stands for number of pixel change rate and UACI is unified avarage change intensity defins as follows [29].
$$UACI = \frac{1}{N} \left[ \sum_{i,j} \frac{ |C1(i,j) – C2(i,j)| }{255} \right]\tag{4}$$
$$NPCR = \frac{\sum_{i,j} D(i,j)}{M \times N} \times 100\% \tag{5}$$
here n and m gives the number of columns and rows respectively. D(i, j) is given by
$$D(i,j) = \begin{cases} 1, & C1(i,j) \ne C2(i,j) \\ 0, & \textit{otherwise} \end{cases}\tag{6}$$
here cipher and original images are given by C2(i, j) and C1(i, j) respectively.
5.5. U I Q(Universal Image Quality Index)
To extract the similarity between cipher and original image we use U I Q. It is ranging from -1 to +1 where the more similarity is indicated by the 1 and least similarity is indicated by -1. Equation for U I Q is [29].
$$UQI(x,y) = \frac{\sigma_{xy}}{\sigma_x \sigma_y} * \frac{2\mu_x \mu_y}{\mu_x^2 + \mu_y^2} * \frac{2\sigma_x \sigma_y}{\sigma_x^2 + \sigma_y^2}
\tag{7}$$
5.6. S S I M(Structural Similarity Index Measure)
U I Q Index’s improved version is S S I M. It is ranging from -1 to +1 where the more similarity is indicated by the 1 and least similarity is indicated by -1. Equation for S S I M is [29].
$$SSIM(x,y) = \left[ \frac{(2\mu_x \mu_y + C1)(2\sigma_{xy} + C2)}{(\mu_x^2 + \mu_y^2 + C1)(\sigma_x^2 + \sigma_y^2 + C2)} \right]\tag{8}$$
here, when the division is done with weak denominator, to stabilize that we use the constants C2 and C1.
Table 1: Results of proposed work
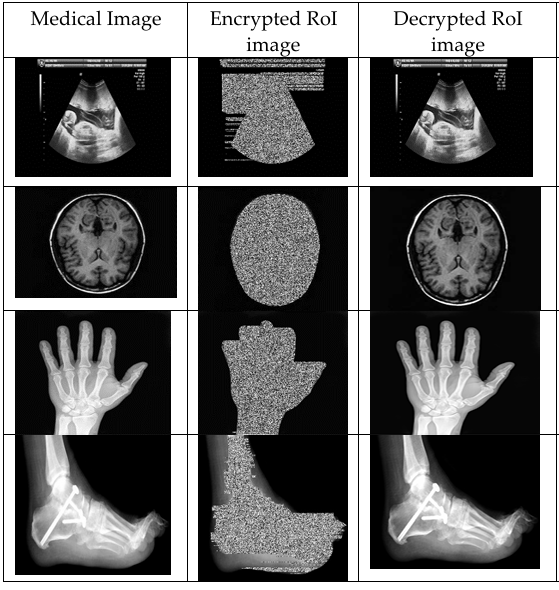
Table 2: ROI based encryption system’s parameters Performance
Image | Entropy Input | Entropy output | M S E | P S N R (db) | N P C R (%) | U A C I (%) | U Q I | S S I M |
Hand | 4.4402 | 6.0012 | 76.62 | 59.89 | 49.07 | 25.10 | 0.74 | 0.42 |
M R I | 4.5598 | 5.9972 | 53.70 | 42.85 | 44.02 | 19.69 | 0.68 | 0.47 |
Foot | 3.7643 | 5.0887 | 89.12 | 72.20 | 46.95 | 30.62 | 0.81 | 0.54 |
Baby | 4.9216 | 6.4233 | 46.13 | 23.95 | 47.89 | 26.68 | 0.60 | 0.46 |
Table 3: ROI based encryption system’s Efficiency
Name of Image | Time elapsed for Encryption (sec) | Percentage of Time saved |
Hand | 0.15953 | 46.6564 |
MRI | 0.17435 | 45.6093 |
Foot | 0.198069 | 39.5001 |
Baby | 0.171694 | 44.7968 |
Table 1 shows the inputs images, encrypted images and decrypted images of proposed system. From Table 2, we conclude that the entropy value of the encoded image is greater than the entropy value of the original simple image. The MSE score is increased based on the image showing the level of encoding. With selective encoding, the NPCR values of the proposed method do not change significantly, the cost and computation time are reduced, and the same metrics are reduced to zero. In other words, the lower the value, the higher the difference between them. Input image and encoded ROI image.
Table 3 shows the effectiveness of the proposed method in terms of speed of implementation and cost. Compared with full-frame encoding, this method saves about 50% of computation cost and provides fast frame-coding execution time. The analysis of the entropy values of the various medical images in Table 2 reveals the high entropy of the new cryptographic algorithms.
Table 2 calculated the SSIM values between the final encoded medical image and the original medical image. Obviously, our method gives a smaller SSIM value. From Table 3, we can see that the coding time for different medical images has been reduced. This is achieved because it performs image selective encoding rather than full encoding, and because it is a lightweight encoding technology, it takes less time to perform bit-plane encoding.
Table 4: Comparison of M R I Image’s Parameter with other method
Parameter | Proposed Technique | Method [30] | Method [31] |
M S E | 53.7086 | 86.2657 | 123.56 |
PSNR (db) | 42.8534 | 10.0881 | 25.45 |
NPCR (%) | 44.0204 | 51.47 | 65.78 |
UACI(%) | 19.6987 | 12.4578 | 18.91 |
S S I M | 0.4718 | 0.4621 | 0.65 |
Encryption Time(secs) | 0.17435 | 72.5001 | 32.25 |
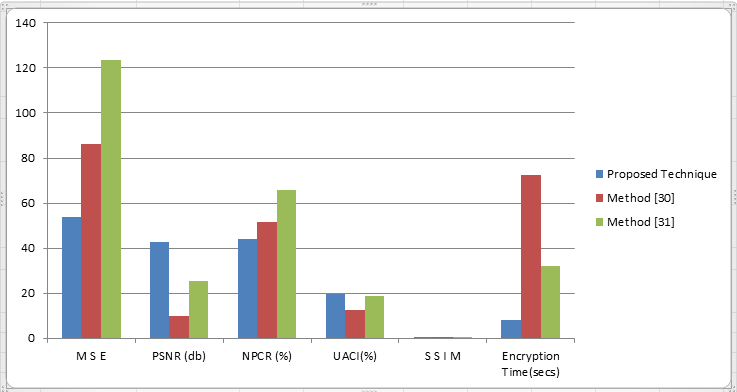
Our method significantly reduces encryption time, ensures the reliability of images sent to the cloud, and ensures security with a two-level encryption scheme. To check the validity of the selective encoding scheme, calculate various parameters such as NPCR, MSE, PSNR, SSIM, and encoding time and compare these values with those obtained by existing methods. Table 4 shows that selective encryption schemes are an effective method because they give better results than existing methods.
6. Conclusion
In this article, we have proposed a method to partially encrypt personal information such as tumors and fetal organs. Traditional image protection technologies have many problems such as data filling up and growing larger as storage space is wasted over time. Furthermore, since the entire image is encrypted, the image cannot be recognized before decryption and sensitive information is leaked after decryption. The problem of conventional sub-image encryption is that the unnecessary parts are encrypted by encrypting a rectangular region consisting of pieces of information requiring security. The proposed method detects important pixels using histogram vertex detection and counts them using Sudoku matrix. In this study, we measure the encryption speed of the proposed method and determine the most suitable block unit for encryption in order to improve the encoding and decoding speed of the image part. Limitation of proposed work is not applicable to binary image encryption.
Conflict of Interest
The authors declare no conflict of interest.
- Satoh, Hitoshi, Noboru Niki, Kenji Eguchi, Hironobu Ohmatsu, Masahiko Kusumoto, Masahiro Kaneko, and Noriyuki Moriyama. “Teleradiology network system on cloud using the web medical image conference system with a new information security solution.” In Medical Imaging 2013: Advanced PACS-based Imaging Informatics and Therapeutic Applications, vol. 8674, pp. 264-272. SPIE, 2013.
- Avudaiappan, T., R. Balasubramanian, S. Sundara Pandiyan, M. Saravanan, S. K. Lakshmanaprabu, and K. Shankar. “Medical image security using dual encryption with oppositional based optimization algorithm.” Journal of medical systems42, no. 11 (2018): 1-11.
- Wang, Chunpeng, Xingyuan Wang, Zhiqiu Xia, and Chuan Zhang. “Ternary radial harmonic Fourier moments based robust stereo image zero-watermarking algorithm.” Information Sciences470 (2019): 109-120.
- Xie, Dong. “Public key image encryption based on compressed sensing.” IEEE Access7 (2019): 131672-131680.
- Zhu, Shuqin, and Congxu Zhu. “Plaintext-related image encryption algorithm based on block structure and five-dimensional chaotic map.” IEEE Access7 (2019): 147106-147118.
- Binjubeir, Mohammed, Abdulghani Ali Ahmed, Mohd Arfian Bin Ismail, Ali Safaa Sadiq, and Muhammad Khurram Khan. “Comprehensive survey on big data privacy protection.” IEEE Access8 (2019): 20067-20079.
- Li, Ming, Pengcheng Wang, Yanfang Liu, and Haiju Fan. “Cryptanalysis of a novel bit-level color image encryption using improved 1D chaotic map.” IEEE Access7 (2019): 145798-145806.
- Manjula, G., and H. S. Mohan. “Probability based selective encryption scheme for fast encryption of medical images.” In ICAICR’19: Proceedings of the Third International Conference on Advanced Informatics for Computing Research, Article, vol. 17, pp. 15-16. 2019.
- Jang, Wonyoung, and Sun-Young Lee. “Partial image encryption using format-preserving encryption in image processing systems for Internet of things environment.” International Journal of Distributed Sensor Networks16, no. 3 (2020): 1550147720914779.
- Sankaradass, Veeramalai, P. Murali, and M. Tholkapiyan. “Region of Interest (ROI) based image encryption with sine map and lorenz system.” In International Conference on ISMAC in Computational Vision and Bio-Engineering, pp. 493-502. Springer, Cham, 2018.
- Mousavi, Seyed Mojtaba, Alireza Naghsh, and S. A. R. Abu-Bakar. “A heuristic automatic and robust ROI detection method for medical image warermarking.” Journal of digital imaging28, no. 4 (2015): 417-427.
- Zhou, Jian, Jinqing Li, and Xiaoqiang Di. “A novel lossless medical image encryption scheme based on game theory with optimized ROI parameters and hidden ROI position.” IEEE Access8 (2020): 122210-122228.
- Rashmi, P., and M. C. Supriya. “Encryption of Color image to enhance security using Permutation and Diffusion Techniques.” International Journal of Advanced Science and Technology28, no. 12 (2019): 375-384.
- Ni, Zhicheng, Yun-Qing Shi, Nirwan Ansari, and Wei Su. “Reversible data hiding.” IEEE Transactions on circuits and systems for video technology16, no. 3 (2006): 354-362.
- Kumar, C. Vinoth, V. Natarajan, and Deepika Bhogadi. “High capacity reversible data hiding based on histogram shifting for medical images.” In 2013 international conference on communication and signal processing, pp. 730-733. IEEE, 2013.
- Yang, Yang, Weiming Zhang, and Nenghai Yu. “Improving visual quality of reversible data hiding in medical image with texture area contrast enhancement.” In 2015 international conference on intelligent information hiding and multimedia signal processing (IIH-MSP), pp. 81-84. IEEE, 2015.
- Wu, Min-Hao, Jianyang Zhao, Bolun Chen, Yongjun Zhang, Yongtao Yu, and Jianhong Cheng. “Reversible data hiding based on medical image systems by means of histogram strategy.” In 2018 3rd international conference on information systems engineering (ICISE), pp. 6-9. IEEE, 2018.
- Huang, Li-Chin, Lin-Yu Tseng, and Min-Shiang Hwang. “A reversible data hiding method by histogram shifting in high quality medical images.” Journal of Systems and Software86, no. 3 (2013): 716-727.
- Yue, X. D., D. Q. Miao, N. Zhang, L. B. Cao, and Qiang Wu. “Multiscale roughness measure for color image segmentation.” Information Sciences216 (2012): 93-112.
- Sastry, S. Sreehari, K. Mallika, B. Gowri Sankara Rao, Ha Sie Tiong, and S. Lakshminarayana. “Liquid crystal textural analysis based on histogram homogeneity and peak detection algorithm.” Liquid Crystals39, no. 4 (2012): 415-418.
- Boukharouba, S., José Manuel Rebordão, and P. L. Wendel. “An amplitude segmentation method based on the distribution function of an image.” Computer vision, graphics, and image processing29, no. 1 (1985): 47-59.
- Elguebaly, Tarek, and Nizar Bouguila. “Bayesian learning of finite generalized Gaussian mixture models on images.” Signal Processing91, no. 4 (2011): 801-820.
- Azam, Muhammad, and Nizar Bouguila. “Unsupervised keyword spotting using bounded generalized Gaussian mixture model with ICA.” In 2015 IEEE Global Conference on Signal and Information Processing (GlobalSIP), pp. 1150-1154. IEEE, 2015.
- Wu, Yue, Yicong Zhou, Joseph P. Noonan, Karen Panetta, and Sos Agaian. “Image encryption using the sudoku matrix.” In Mobile Multimedia/Image Processing, Security, and Applications 2010, vol. 7708, pp. 222-233. SPIE, 2010.
- Ahmad, Jawad, and Fawad Ahmed. “Efficiency analysis and security evaluation of image encryption schemes.” computing23 (2010): 25.
- Zhang, Xuncai, Lingfei Wang, Guangzhao Cui, and Ying Niu. “Entropy-based block scrambling image encryption using DES structure and chaotic systems.” International Journal of Optics2019 (2019).
- Wu, Yue, Joseph P. Noonan, and Sos Agaian. “NPCR and UACI randomness tests for image encryption.” Cyber journals: multidisciplinary journals in science and technology, Journal of Selected Areas in Telecommunications (JSAT)1, no. 2 (2011): 31-38.
- Wang, Zhou, Alan C. Bovik, Hamid R. Sheikh, and Eero P. Simoncelli. “Image quality assessment: from error visibility to structural similarity.” IEEE transactions on image processing13, no. 4 (2004): 600-612.
- Wang, Zhou, and Alan C. Bovik. “Modern image quality assessment.” Synthesis Lectures on Image, Video, and Multimedia Processing2, no. 1 (2006): 1-156.
- Sajjad, Muhammad, Khan Muhammad, Sung Wook Baik, Seungmin Rho, Zahoor Jan, Sang-Soo Yeo, and Irfan Mehmood. “Mobile-cloud assisted framework for selective encryption of medical images with steganography for resource-constrained devices.” Multimedia Tools and Applications76, no. 3 (2017): 3519-3536.
- Akkasaligar, Prema T., and Sumangala Biradar. “Selective medical image encryption using DNA cryptography.” Information Security Journal: A Global Perspective29, no. 2 (2020): 91-101.
