Offline Signature Verification based on Edge Histogram using Support Vector Machine
 , Kiran2
, Kiran2 , Sudheesh Kannur Vasudeva Rao2
, Sudheesh Kannur Vasudeva Rao2 and Yashwanth Jagadeesh2
and Yashwanth Jagadeesh2
Journal of Engineering Research and Sciences, Volume 1, Issue 5, Page # 160-166, 2022; DOI: 10.55708/js0105017
Keywords: Signature, Recognition, SVM, Forgery, Genuine
(This article belongs to the Special Issue on SP1 (Special Issue on Multidisciplinary Sciences and Advanced Technology 2022) and the Section Interdisciplinary Applications – Computer Science (IAC))
Export Citations
Cite
Sannappa, S. K. D. , Kiran, , Rao, S. K. V. and Jagadeesh, Y. (2022). Offline Signature Verification based on Edge Histogram using Support Vector Machine. Journal of Engineering Research and Sciences, 1(5), 160–166. https://doi.org/10.55708/js0105017
Sunil Kumar Dyavaranahalli Sannappa, Kiran, Sudheesh Kannur Vasudeva Rao and Yashwanth Jagadeesh. "Offline Signature Verification based on Edge Histogram using Support Vector Machine." Journal of Engineering Research and Sciences 1, no. 5 (May 2022): 160–166. https://doi.org/10.55708/js0105017
S.K.D. Sannappa, Kiran, S.K.V. Rao and Y. Jagadeesh, "Offline Signature Verification based on Edge Histogram using Support Vector Machine," Journal of Engineering Research and Sciences, vol. 1, no. 5, pp. 160–166, May. 2022, doi: 10.55708/js0105017.
Investigation on verification of offline signature has explored a huge sort of techniques on more than one signature datasets, which can be amassed beneath managed conditions. However, these records will not necessarily reflect the characteristics of the signatures in some useful use cases. In this work, introduced a novel feature representation technique called edge histogram and 4 directional histograms for offline signature verification system. For classification of signature support vector machine (SVM) technique employed. Edge is a curve or point where the intensity of an image changes rapidly. Edges represent the boundary of object of an image. Edge detection is a process of detecting edges of an image. Several algorithms are available to detect edges effectively from an image. Canny, Roberts, Prewitt and Sobel are several popular available edge detectors.
1. Introduction
Signatures are behavioral biometric traits of a person, used to authenticate a person. In all the legal transaction and documentations signature is required to authenticate its legality. In such cases there may be chances to forge the signature by someone to get the benefits. Therefore in order to check the genuineness of the signature, signature authentication system is required. There are several algorithms are proposed by different authors but still there are challenges to address the skilled forgery and intra class variation.
Traditional cashier examinations, bank loans, credit cards and various legal documents has become a staple of modern work. Unavoidable the side effect of signing is that it can be used to make a document look like it is genuine. As a result, there is a growing need for research on efficient automation solutions for recognizing and validating signatures. The signature verification system aims to automatically distinguish whether the biometric sample is actually from the requested individual. That is, it is used to determine whether a query signature is fake or real. Fake is usually classified. It can be divided into three types: simple, random, and clever (or simulated) fake. The counterfeiter has no information about the user or his signature when they counterfeit randomly. Instead, the counterfeiter uses his own sign. In this instance, the fake carries something else that means more than the user’s actual signature. It has a completely different shape overall. It’s just a fake, and the fake knows only the user’s name, not the signature. In this case, especially if it is fake, it indicates that it resembles a real signature. An individual who signs with their entire name or a portion of it. In the subject Counterfeiters, counterfeiters have access to the user’s name. Sign and frequently practice spoofing a user’s signature. This leads to a more similar fake. It is difficult to recognize because it is an actual signature.
2. Related Work and Motivation
In [1, 2], the authors proposed a new convolutional neural network model called Large-Scale Signature Network (LS2Net), which is aimed to address the problem of small number of signature sets to train the model from large dataset. Authors introduce Class Center based Classification (C3) to classify embedded features. C3 uses class centers which are achieved by averaging in-class properties. Under these class centers, 1-nearest neighbor classifier is derived as classification task. Authors also addressed Large-Scale recognition problem, the influence of Leaky ReLU on the performance of network is examined. Along with the addition of the C3 (Class Center for Classification) algorithm, the default network is defined as C3+BN+LS2Net called as LS2Net_v2. In [3] author has presented fusion of two methods one is Curvelet Transform (CT) and another is One-Class Principal Component Analysis (OC PCA) for Open Handwritten Signature Identification System. In [4,5,6] author has presented back propagation method of Neural Networks. If the output obtained at output layer having higher error rate then it can be propagate back to the previous layers to minimize the error by adjusting the weights of the nodes of the hidden layers, where the data processes again and gives the result at output layer. This process repeats until the desired output obtained with minimum error rate. In [7]-[9], authors has presented a Back Propagation Artificial Neural Network Matching Technique for offline signature verification. The suggested model consists pre-processing phase, codebook generation phase and matching phase. In [10], authors propose a method that uses the information from DTW cost matrix and warping paths alignments. The decision is made by the conjunction of warping path score and DTW score. In signature verification, solid signatures may be damaged up into 3 one-of-a-kind classes. In [11, 12], authors used Extreme point and stroke point for recognition. In addition, some works make a fusion of DTW with other methods. In [13], author has presented fuse the Fast Fourier Transform with DTW and the fusion system lowers the error rate by up to about 25%. In [14], authors explained how to extract a set of features for comparing DTWs based on dissimilarities between test signatures and template databases. In addition, the closest submission and majority vote will be proposed for classification. In [15] – [17], author has presented model-based approach is a generation classifier like the Hidden Markov Model (HMM). In [18, 19, 20] author has presented a neural network (NN) based signature recognition. In [21, 22] author has presented support vector machine (SVM) based offline signature recognition system. In [23] author explained the use one of the discriminating classifiers. There are also some hybrid methods that combine the various methods described above. In [24, 25], author has presented a multi-level cascade framework and multi-level decision level score fusion or a multi-expert system for signature verification has been reported in the literature. In [26, 27], author has explained several RNN-based validation methods have recently been proposed. In [28], authors propose a new descriptor called the Length Normalized Path Signature (LNPS) for feature representation, which is then fed to the GRU (Gated Recurrent Unit) network. We trained the network with the BP algorithm using triplet loss and center loss. In [29], author has explained how to extracts 23 hand-crafted time function features and uses bidirectional LSTM (long short-term memory) and a Siamese architecture GRU network to learn dissimilarity metrics from signature pairs. In [30], author has presented the distance-based and model-based approaches are the two main methods. In [31], author has explained design context and functionality and a two-step strategy for accurate online signature verification. In particular, in the first stage, shape context features are extracted from the input and the classification is based on distance metrics. In [32], author has presented the optimum feature subspace is selected according to the contribution rate. In addition, to solve the problem of large-scale DTW computation, we proposed a simple and effective modified dynamic time warping (DTW) with signature curve constraints. In [33] author has presented the DCT technique to get a compact representation of your online signature using a fixed number of coefficients. This simplifies the fitting procedure and provides an effective alternative for working with time series of varying lengths.
There are both writer-independent and writer-dependent signature verification methods in the literature. However, in the actual signature verification settings, the user Registration is very common. For this the writer-dependent method is not applicable. In Writer-independent methods, the themes for training and testing are different, so personal characteristics are not possible. It will be used. Writer-independent methods try to learn efficient representation of signatures in order to distinguish them from each other. As a person, creating a universally discriminatory expression of a signature is a challenge, not a specialty. I found an extraction method to solve this problem.
To improve the accuracy and efficiency of matching, use the edge histogram function and SVM to compare the test signature with the registered reference signature based on the extracted features. A classifier based on the symbolic representation of interval values is proposed to determine if the test signature is genuine.
The contributions of this paper are as follows:
- A fast and accurate edge histogram-based SVM method is proposed based on the fact of the imbalanced probability of occurrence of clever and random signature forgery.
- Edge histogram feature Extractor was developed to describe the global shape features of signatures for fast classification of random counterfeiting, along with basic pre-processing that applies to all records.
- SVM applied to fulfil comparison task and interval valued based representation classifier is proposed for final decision making to achieve state of the art verification performance
- The rest of the work consists of: Section 2 reviews related work. The presented method is described in Section 3. Experiment setup and the corresponding result is Section 4. Finally, complete the work in Section 5.
3. Proposed Method
We are going to use novel approach for signature verification using Support Vector Machine classifier. Figure 1 shows the flowchart of proposed offline signature verification system. This system will use static as well as dynamic features for verification. The static functions include momentary functions and 4 direction distribution, while the dynamic functions include gray distribution and stroke width distribution.
Finally, the signature is categorized by support vector machines.
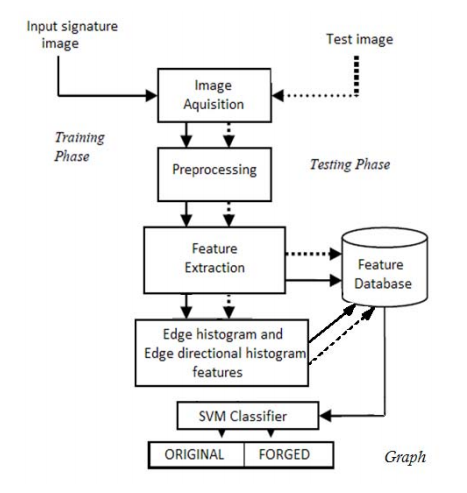
3.1. Signature Enrolment
In the first phase, to find the parameters which characterize the variance of the signatures which are used as a reference, we use a set of signatures for reference. The extracted parameters along with the set of reference signatures are stored in the system database with unique user identification.
3.2. Preprocessing
Preprocessing stage can be divided further in five parts:
3.2.1. Noise Reduction
It’s the process of removing noise from the image. It can be done by using median filters. The widely used noise type is salt and pepper noise. The noise present in the image is certainly degrades the image and it is difficult to select the exact features. To obtain usable information, noise must be removed.
3.2.2. Image Binarization
The acquired image sample may be in different colour model like RGB, gray scale or binary. The advantage of converting to binary scale is, processing will become easy because the intensity of the image will be in 0 and 1 range. There are several algorithms are available to convert, we employed Otsu’s method.
3.2.3. Data Area Cropping
Image cropping is the processes where the image data area is extracted from the background area. Usually offline signature samples are acquired using a paper sheet; signatures are not spread across whole paper but on some portion of the paper. The data sample is the region of interest, so extracting only data area from the background and processing it, will helps in getting better accuracy.
3.2.4. Width Normalization
As we know signature samples are collected from different contributors, so obviously there will be more variations in the sample signatures, during pre-processing stage its necessary to normalize the data samples not only scaling but also its width. Width is one of the local features and varies from sample to sample. Normalized width will helps to get better accuracy.
3.2.5. Image Thinning
It’s the process of keeping one pixel width information and removing redundant pixels. The collected samples are written on a paper, which having different pen width. Thinning operation makes uniform pixel width and also reducing pixel width will minimize the processing time.
3.3. Feature Extraction and Training the model
The study adopted HOG as a feature Extraction technology for recognition and authentication Signature image. Theoretically, the HOG descriptor method is important Occurrence of localized gradient orientation an image or part of a region of interest (ROI). Divide the image into smaller contiguous zones Calculate the histogram of (cell) and each area Gradation direction or edge direction Use pixels in cells, then gradients Receive orientation. Then discretise each Put the cells in a square bin, then the pixels in each cell gives a weighted gradient to the corresponding gradient.
3.4. Signature Verification
Let`s have an perception in SVM. Signatures are usually represented with the aid of using sparse vectors beneath the vector area model. When schooling classifiers on huge collections of signature, each the time and reminiscence necessities related with those vectors can be prohibitive. This requires using a characteristic choice approach now no longer most effective to lessen the quantity of capabilities however additionally to boom the sparsity of vectors. We advise a characteristic choice approach primarily based totally on linear Support Vector Machines (SVMs). Linear SVM is used on a subset of schooling facts to teach a linear classifier that is characterised with the aid of using the ordinary to the hyper aircraft dividing fantastic and bad instances.
Components of the everyday with better absolute values have a bigger effect on statistics classification. Instead of predefining the quantity of maximum scoring capabilities to be protected in a classifier we practice characteristic choice that targets at a predefined common sparsity stage throughout files and classifiers for a given schooling set. After the characteristic set is determined, the version is educated on the entire schooling statistics set represented in the decided on characteristic set. The check signature is then, primarily based totally on its price for the parameters from the characteristic set, is mapped and categorized as “GENUINE” or “FORGED”.
4. Experimentation
The following figure is the snapshot of Graphical User Interface for Offline Signature Verification developed using GUID tool available in MATLAB. Experiments are conducted on benchmark datasets namely CEDAR (Center for Document Analysis and Recognition) and GPDS Synthetic Signature database. The know-how repository includes the TSE capabilities extracted from each signature pattern of the records set such as each proper and professional forge signature samples. With every dataset, the signature samples are categorized into two groups: the education pattern set and the trying out pattern set with various wide variety of samples. We have achieved 4 units of experiments. With Set-1, the first 10 proper and primary ten professional fakes are selected as education samples and compared with the ultimate samples of the respective datasets. With Set-2, the first 15 samples of proper and primary 15 samples of professional fakes are considered and compared with the ultimate samples of the dataset. In Set3, we randomly selected 10 real samples and 10 randomly selected fake samples for training and tested them on the remaining samples in the dataset. Also, in Set4, there are 15 samples randomly selected from each dataset for training, the remaining samples are the sample in question. In order to overcome the influence of randomness, the experiments of Set3 and Set4 are repeated 5 times and the average results are tabulated. Achieved 97 ° and 98 ° accuracy with the CEDAR dataset.
The signature verification efficiency is evaluated by two parameters: (i) false acceptance rate (F A R) and (ii) false rejection rate (F R R). Recognition rate is one more parameter to consider when assessing classifier performance.
Type I error or False Rejection Rate (F R R):
$$\text{FAR} = \frac{\text{No. of forged signatures identified as genuine}}{\text{No. of forged signature samples}} \times 100\%\tag{1}$$
Type II error or False Acceptance Rate (F A R):
$$\text{FAR} = \frac{\text{No. of forged signatures identified as genuine}}{\text{No. of forged signature samples}} \times 100\%\tag{2}$$
Recognition rate: The classifier accuracy is identified by this parameter, which is given by:
$$\text{Recognition rate} = \frac{\text{No. of correctly indentified signature samples}}{\text{No. of signature samples}} \times 100\%\tag{3}$$
Equal Error Rate (EER): Which is the error when false acceptance rate is equal to false rejection rate.
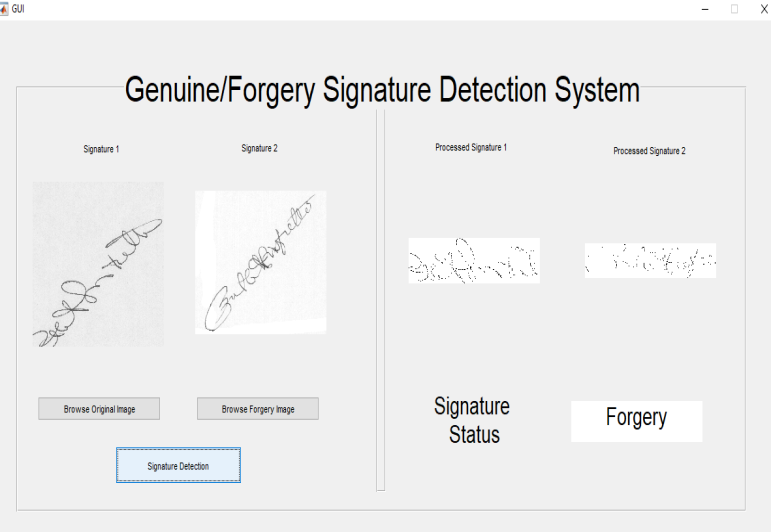
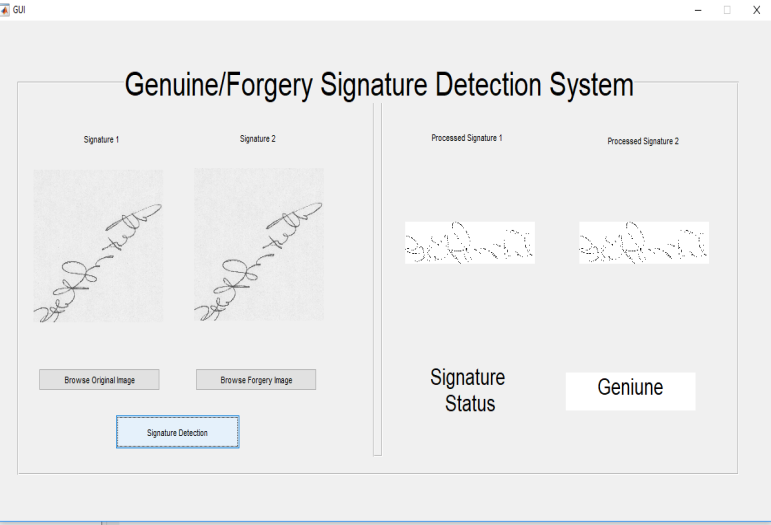
For testing the signature detection system. We have considering 50 signatures in that 30 signatures are genuine and 20 signatures are forgery.
Table 1: Results of proposed SVM method
Users | No. of signature | FRR | FAR | Accuracy |
User1 | 50 | 5/50=10% | 3/50=6% | 45/50=90% |
User 2 | 50 | 3/50=6% | 4/50=8% | 47/50=94% |
User 3 | 50 | 4/50=8% | 2/50=4% | 46/50=92% |
Table 2: Comparisons with the state-of-the-art works on database SVC2004.
Works | Method | Error Rate (%) |
[28] | LNPS+GRU | 2.47 |
[29] | GMM+DTW with SCC | 2.63 |
[30] | DTW+ Warping path alignment | 2.53 |
[31] | Two-stage verification | 2.39 |
[32] | DTW with SCC | 2.89 |
[33] | Spare representation | 2.98 |
Proposed Work | Edge Histogram + SVM | 2.37 |
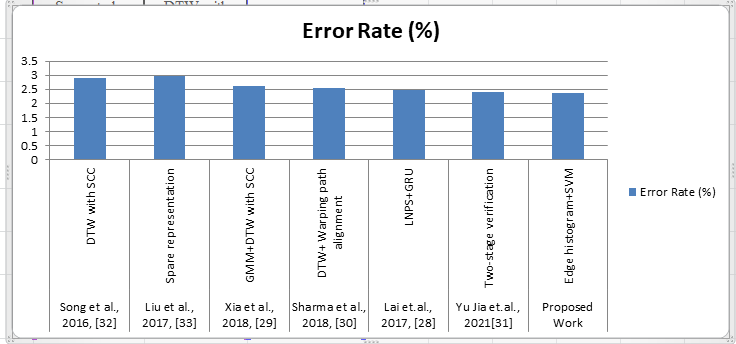
Table 2 shows a comparison of the SVC2004 database with the prior art. Due to the different databases, training, tests, etc., it is not easy to make a fair comparison of online signature verification methods. Select some recently published works using the same database (SVC2004). The existing method has a slightly higher EER than our method.
5. Conclusion
Offline signature verification based on edge histograms using a support vector machine system has been proposed. Using techniques such as RGB2Gray conversion, filtering, adjustment, thresholding, and clever edge detection, the signature can be pre-processed. It has been shown here that the proposed method is more efficient and thoroughly tested to detect segmented signatures of the original image with different image processing methods. The proposed work limitation is that the classifier is retrained during the training phase. In Future work, the support vector machine (SVM) is being examined for the discovery task.
Conflict of Interest
The authors declare no conflict of interest.
- Nurullah Çalik, Onur Can Kurban, Ali Rıza Yilmaz, Tulay Yildirim, Lütfiye Durak Ata, Large-scale offline signature recognition via deep neural networks and feature embedding, Neurocomputing, Volume 359, 2019, Pages 1-14, ISSN 0925-2312,https://doi.org/10.1016/j.neucom.2019.03.027.
- Bilal Hadjadji, Youcef Chibani, and Hassiba Nemmour.An efficient open system for offline handwritten signature identification based on curvelet transform and one-class principal component analysis. Neurocomput. 265, November 2017, 66–77. DOI: 10.1016/j.neucom.2017.01.108
- Rahmi, Asyrofa & Wijayaningrum, Vivi Nur & Mahmudy, Wayan & a K Parewe, Andi. Offline Signature Recognition using Back Propagation Neural Network. Indonesian Journal of Electrical Engineering and Computer Science. 4. (2016). x-y. 10.11591/ijeecs.v4.i3.pp678-683.
- Yahy, Anwar & Sulong, Ghazali. Offline handwritten signature verification using back propagation artificial neural network matching technique. Journal of Theoretical and Applied Information Technology. 65. (2014). 790-800.
- Indrajit Bhattacharya, Prabir Ghosh, Swarup Biswas, Offline Signature Verification Using Pixel Matching Technique, Procedia Technology, Volume 10,2013,Pages 970-977, ISSN 2212-0173, https://doi.org/10.1016/j.protcy.2013.12.445.
- Kruthi, C. and Deepika C. Shet. “Offline Signature Verification Using Support Vector Machine.” 2014 Fifth International Conference on Signal and Image Processing(2014): 3-8. DOI:1109/ICSIP.2014.5
- Guerbai, Yasmine & Chibani, Youcef & Hadjadji, Bilal. (2015). The effective use of the one-class SVM classifier for handwritten signature verification based on writer-independent parameters. Pattern Recognition. 48. 103–113. 10.1016/j.patcog.2014.07.016.
- Ghosh, Rajib & Kumar, Pradeep & Roy, Partha. (2019). A Dempster–Shafer theory based classifier combination for online Signature recognition and verification systems (https://rdcu.be/bbNHo).. International Journal of Machine Learning and Cybernetics. 10.1007/s13042-018-0883-9.
- Jagtap, A.B., Hegadi, R.S. and Santosh, K.C.,. Feature learning for offline handwritten signature verification using convolutional neural network. International Journal of Technology and Human Interaction (IJTHI), Vol.15(4), 2019, pp.54-62. DOI: 4018/IJTHI.2019100105.
- Bhunia, Ankan & Alaei, Alireza & Roy, Partha. Signature Verification Approach using Fusion of Hybrid Texture Features. Neural Computing and Applications. (2019). 10.1007/s00521-019-04220-x.
- Hao Feng, Chan Choong Wah, Online signature verification using a new extreme points warping technique, Pattern Recognition Letters, Volume 24, Issue 16, 2003, Pages 2943-2951, ISSN 0167-8655, https://doi.org/10.1016/S0167-8655(03)00155-7.
- Kar, Biswajit & Mukherjee, Anirban & Dutta, Pranab. Stroke Point Warping-Based Reference Selection and Verification of Online Signature. IEEE Transactions on Instrumentation and Measurement. (2017). PP. 1-10. 10.1109/TIM.2017.2755898.
- Yanikoglu, Berrin & Kholmatov, Alisher). Online Signature Verification Using Fourier Descriptors. Journal on Advances in Signal Processing. 2009. 10.1155/2009/260516.
- Chen, Zhili, Xinghua Xia and Fang-jun Luan. “Automatic online signature verification based on dynamic function features.” 7th IEEE International Conference on Software Engineering and Service Science (ICSESS)(2016): 964-968. DOI:1109/ICSESS.2016.7883226.
- Bao, Ly & Garcia-Salicetti, Sonia & Dorizzi, Bernadette, On Using the Viterbi Path Along With HMM Likelihood Information for Online Signature Verification. IEEE transactions on systems, man, and cybernetics. Part B, Cybernetics : a publication of the IEEE Systems, Man, and Cybernetics Society. 37. (2007). 1237-47. 10.1109/TSMCB.2007.895323.
- Muramatsu, M. Kondo, M. Sasaki, S. Tachibana and T. Matsumoto, “A Markov chain Monte Carlo algorithm for bayesian dynamic signature verification,” in IEEE Transactions on Information Forensics and Security, vol. 1, no. 1, pp. 22-34, March 2006, doi: 10.1109/TIFS.2005.863507.
- Fierrez, Julian & Ortega-Garcia, Javier & Ramos, Daniel & Gonzalez-Rodriguez, Joaquin. (2007). HMM-based on-line signature verification: Feature extraction and signature modeling. Pattern Recognition Letters. 28. 2325-2334. 10.1016/j.patrec.2007.07.012.
- Fuentes, S. Garcia-Salicetti and B. Dorizzi, “On line signature verification: Fusion of a Hidden Markov Model and a neural network via a support vector machine,” Proceedings Eighth International Workshop on Frontiers in Handwriting Recognition, 2002, pp. 253-258, doi: 10.1109/IWFHR.2002.1030918.
- Lejtman, Dariusz & George, Susan. On-line Handwritten Signature Verification Using Wavelets and Back-propagation Neural Networks.. 992-996. 2001. 10.1109/ICDAR.2001.953934.
- Rashidi, Saeid & Fallah, Ali & Towhidkhah, Farzad. (2012). Feature extraction based DCT on dynamic signature verification. Scientia Iranica. 19. 1810–1819. 10.1016/j.scient.2012.05.007.
- Gruber, Christian & Gruber, Thiemo & Krinninger, Sebastian & Sick, Bernhard. Online Signature Verification With Support Vector Machines Based on LCSS Kernel Functions. IEEE transactions on systems, man, and cybernetics. Part B, Cybernetics : a publication of the IEEE Systems, Man, and Cybernetics Society. 40. 2009. 1088-100. 10.1109/TSMCB.2009.2034382.
- Swanepoel and J. Coetzer, “Feature Weighted Support Vector Machines for Writer-Independent On-Line Signature Verification,” 2014 14th International Conference on Frontiers in Handwriting Recognition, 2014, pp. 434-439, doi: 10.1109/ICFHR.2014.79.
- Ning-Ning Liu and Yun-Hong Wang, “Fusion of global and local information for an on-line Signature Verification system,” 2008 International Conference on Machine Learning and Cybernetics, 2008, pp. 57-61, doi: 10.1109/ICMLC.2008.4620378.
- Fierrez, Julian & Nanni, Loris & Lopez-Peñalba, Jaime & Ortega-Garcia, Javier & Maltoni, Davide. An On-Line Signature Verification System Based on Fusion of Local and Global Information. 3546. 2005. 523-532. 10.1007/11527923_54.
- Kiran, P. & B D, Dr Parameshachari & Yashwanth, J. & Bharath, K.. Offline Signature Recognition Using Image Processing Techniques and Back Propagation Neuron Network System. SN Computer Science. 2. 2021. 1007/s42979-021-00591-y.
- L. Bovino, S. Impedovo, G. Pirlo and L. Sarcinella, “Multi-expert verification of hand-written signatures,” Seventh International Conference on Document Analysis and Recognition, 2003. Proceedings., 2003, pp. 932-936, doi: 10.1109/ICDAR.2003.1227796.
- Liang Wan, Bin Wan and Lin Z-C, “On-line signature verification with two-stage statistical models,” Eighth International Conference on Document Analysis and Recognition (ICDAR’05), 2005, pp. 282-286 Vol. 1, doi: 10.1109/ICDAR.2005.175.
- Lai, Songxuan & Jin, Lianwen & Yang, Weixin. Online Signature Verification Using Recurrent Neural Network and Length-Normalized Path Signature Descriptor. 400-405. 2017. 10.1109/ICDAR.2017.73.
- Xinghua Xia, Xiaoyu Song, Fangun Luan, Jungang Zheng, Zhili Chen, Xiaofu Ma, Discriminative feature selection for on-line signature verification, Pattern Recognition, Volume 74, 2018, Pages 422-433, ISSN 0031-3203, https://doi.org/10.1016/j.patcog.2017.09.033.
- Sharma, Abhishek & Sundaram, Suresh. On the Exploration of Information From the DTW Cost Matrix for Online Signature Verification. IEEE Transactions on Cybernetics. 2017. 1-14. 10.1109/TCYB.2017.2647826.
- Jia, Yu & Huang, Linlin & Chen, H-J. A Two-Stage Method for Online Signature Verification Using Shape Contexts and Function Features. Sensors. 19. 2019. 1808. 10.3390/s19081808.
- Song, X. Xia and F. Luan, “Online Signature Verification Based on Stable Features Extracted Dynamically,” in IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 47, no. 10, pp. 2663-2676, Oct. 2017, doi: 10.1109/TSMC.2016.2597240.
- Liu, Yishu & Yang, Zhihua & Yang, Lihua. Online Signature Verification Based on DCT and Sparse Representation. IEEE transactions on cybernetics. 45. 2014.10.1109/TCYB.2014.2375959.
- Sunil Kumar Dyavaranahalli Sannappa, Kiran, Sudheesh Kannur Vasudeva Rao, Yashwanth Jagadeesh, “A Computational Approach for Recognizing Text in Digital and Natural Frames”, Journal of Engineering Research and Sciences, vol. 3, no. 7, pp. 53–58, 2024. doi: 10.55708/js0307005
- Sunil Kumar Dyavaranahalli Sannappa, Kiran, Sudheesh Kannur Vasudeva Rao, Yashwanth Jagadeesh, “Smart Monitoring System for Housing Societies based on Deep Learning and IoT”, Journal of Engineering Research and Sciences, vol. 2, no. 12, pp. 15–22, 2023. doi: 10.55708/js0212003
- Sunil Kumar Dyavaranahalli Sannappa, Kiran, Sudheesh Kannur Vasudeva Rao, Yashwanth Jagadeesh, “Real-Time Acquisition and Classification of Electrocardiogram Signal”, Journal of Engineering Research and Sciences, vol. 1, no. 11, pp. 8–15, 2022. doi: 10.55708/js0111002
- Sunil Kumar Dyavaranahalli Sannappa, Kiran, Sudheesh Kannur Vasudeva Rao, Yashwanth Jagadeesh, “Cascaded Keypoint Detection and Description for Object Recognition”, Journal of Engineering Research and Sciences, vol. 1, no. 3, pp. 164–169, 2022. doi: 10.55708/js0103017
- Sunil Kumar Dyavaranahalli Sannappa, Kiran, Sudheesh Kannur Vasudeva Rao, Yashwanth Jagadeesh, “An Overview on Various Techniques used for Correct Interpretation of Roadway Symbols”, Journal of Engineering Research and Sciences, vol. 1, no. 3, pp. 28–38, 2022. doi: 10.55708/js0103004
