Blockchain Based Framework for Securing Students’ Records
Journal of Engineering Research and Sciences, Volume 1, Issue 6, Page # 45-54, 2022; DOI: 10.55708/js0106006
Keywords: Blockchain, Encryption, Framework, Records, Security
(This article belongs to the Section Cybernetics – Computer Science (CYC))
Export Citations
Cite
Sarjiyus, O. and Isaiah, I. (2022). Blockchain Based Framework for Securing Students’ Records. Journal of Engineering Research and Sciences, 1(6), 45–54. https://doi.org/10.55708/js0106006
Omega Sarjiyus and Israel Isaiah. "Blockchain Based Framework for Securing Students’ Records." Journal of Engineering Research and Sciences 1, no. 6 (June 2022): 45–54. https://doi.org/10.55708/js0106006
O. Sarjiyus and I. Isaiah, "Blockchain Based Framework for Securing Students’ Records," Journal of Engineering Research and Sciences, vol. 1, no. 6, pp. 45–54, Jun. 2022, doi: 10.55708/js0106006.
Right now, colleges, as focuses of exploration and development, coordinate in their cycles different advances that permit further developing administrations and cycles for their individuals. Among the inventive innovations is the Web of Things that permits getting information from the climate and individuals through various gadgets. Security of information on college grounds is expected to shield basic information and data from unapproved parties. One way of ensuring information is to apply the study of blockchain innovation to perform information encryption. There is a wide assortment of calculations utilized to encrypt information; however, this exploration centers around the SHA-256 encryption. Subsequently, this examination is pointed toward fostering a blockchain-based structure framework for getting understudies' records. These outcomes lead to further developing cycles and settling on better choices that further develop the administrations accessible at the college. Blockchain innovation is otherwise called appropriated record innovation, and It permits members to get the settlement of exchanges, accomplish the exchange, and move resources for a minimal price. In this manner, an examination will be done on the blockchain empowered college framework for getting understudies' records. The framework advancement philosophy taken on to improve this framework is the cascade procedure and Laravel for programming. Blockchain innovation can assist clients with putting away understudy records securely.
1. Introduction
As of now, the utilization of arising advancements has dramatically filled in the public arena, and this has permitted working on numerous parts of personal satisfaction [1]. The improvement that these advancements have carried is predominantly because of the entrance of the Web, which has made enormous enterprises support the plan and making of gadgets that cooperate with individuals or with one another, using the Web [2]. These gadgets have better execution, and their dynamic correspondence with individuals considers their association in most everyday exercises [3]. Indeed, a few of these gadgets are not centered around close-to-home use; however, all things considered, they are centered around taking care of issues in conditions where hundreds or thousands of individuals reside. The speed at which society works brings about innovations that perform exercises that individuals would regularly prefer not to do themselves [4]. Starting here of view, the obligation of controlling the exhibition of an action shared with the gadgets should be possible distantly. These qualities of the gadgets make them part of the Web of Things (IoT) [5]. The IoT permits the association of numerous gadgets to the organization through sensors and actuators that play out an assortment of errands [6]. These assignments can be intended for homegrown use or in exceptionally enormous conditions, such as grounds or urban communities, where their fundamental task is gathering data from the climate and playing out an activity [7]. A proof of this is home mechanization, which has customarily required private innovation to work appropriately. With the utilization of IoT, this methodology has changed. Presently, such stages are accessible, and advancement is centered around the improvement of uses that utilization the administrations of different stages to perform more intricate errands [8]. The IoT has situated itself as one of the mainstays of the advanced climate. This way, conventional conditions use data innovation (I.T.), remembered for designs that work close by, arising advancements to give the climate some knowledge [9]. A progressively apparent model is keen urban communities. These large-scale conditions have an endless number of administrations that need IoT to work on their utilization, particularly in regions like versatility and security [6].
What’s more, ideas, for example, human digital actual frameworks to screen, control, and oversee conditions proficiently, are coordinated determined to guarantee sufficient conditions at a lower cost [10,11]. These frameworks are worked from the straightforward coordination of physical and computational parts. These frameworks beat the present straightforward coordinated frameworks as far as limiting flexibility, versatility, strength, security, and ease of use [12].
IoT deals with the administrations of a climate through its design, which is underlying layers and given the assortment of data. The gadgets consistently sense the medium, producing a huge volume of information that goes about as a natural substance for distributed computing [13]. The activity of IoT, even though it presents special benefits to develop client experience further, likewise presents a few issues that have happened definitively in the information procurement layer and how they are shipped [14]. This puts client and association information in danger because, as per reports and exploration on IoT security, there are points of reference in which security levels have been compromised and data has been influenced [15]. These insufficiencies need to do straightforwardly with the incredible second that passes the gadgets that fuse this innovation. This has driven makers to zero in on the offer of an item and not on the nature of the gadget that should fulfill guidelines that permit it to give significant degrees of wellbeing. Large numbers of the security imperfections found in the IoT incorporate makers that leave indirect accesses open to get data about the utilization of their items and, in this manner, work on their business [16]. Data the board is presently an issue that ought to be viewed as a need in sending any engineering that incorporates the utilization of arising advancements. Some arrangements and guidelines are being chipped away at to save information security, and yet, search for models that guarantee the appropriate utilization of data. The blend of innovations has frequently permitted us to work on a framework, design, or show and fortify its utilization in the public eye [17]. This reference is material in the utilization of arising advances, and there are explicit cases that indicate the strength of this mix [2]. This is the situation of college grounds that take on the Web of Things, Enormous Information, and distributed computing to become brilliant grounds [18]. The need is the personalization of the administrations committed to all individuals and producing economic environments [19]. Inside this equivalent climate, the reconciliation of an innovation that, like IoT, has outstanding development, the blockchain, has been thought of. The blockchain is a novel library concurred and appropriated in a few hubs of an organization. This innovation permits the exchange of computerized information with extremely modern coding and protected manner [20]. Each square has a particular and steadfast spot in the chain since each square contains data from the past block’s hash. The whole chain is put away in every hub of the organization that makes up the blockchain, so a precise chain is put away for all organization members [21].
Blockchain innovation turns into the ideal accomplice for IoT because it ensures that data treatment and instability in the client vanishes by not uncovering data from the source and the beneficiary. This is ideal for IoT sending, tackling the issues it presents until now [22]. In any case, how a blockchain engineering can be incorporated into the IoT design without influencing the accessible administrations of a climate? The appropriate response is to make test seats, where these advances are executed in a controlled climate, and the information isn’t compromised. To do this, the work proposes to make a design that incorporates both the IoT and the blockchain inside college grounds [23]. College fields can be pretty much as extensive as little urban areas and handle comparable administration models. The benefit of making this engineering on college grounds is to give the ideal controlled climate and characterize every one of the genuine factors of a scaled climate.
2. Review of Related works
In [24], the authors stated that to further develop learning, there is a tool stash that can become rehearsed for understanding the hypothesis of IoT and blockchain innovation. The instruments comprise of three sections, the “mind,” “muscle,” and “cloud.” Raspberry Pi is utilized as a “cerebrum” of activity that speaks with the Kaiser Cloud stage. The outcomes demonstrate that the learning instruments effectively associate with the Kaiser Cloud stage and can be applied as a training gadget for learning destinations [24]. This exploration expects to present a solid framework dependent on blockchain to determine the trouble of point synchronization in IoT. This review has some advantage of level inactivity through utilizing an assent gadget dependent on evidence of dependability. Squeezing assessments and reproductions demonstrate that this plan vessel effectively opposes not well-arranged uses and diminishes inactivity from the agreement strategy by coordinating with it with old strategies [25]. A concentrate by [26] on the different strides of key casing extraction from a video upheld by secure and progressed transportation to clients offered a technique that permits clients to audit a video dependent on people and items as boundaries. Cryptographic hashes are utilized, including blockchain, and hashes are made from diminished video hinders, communicated, and moved through blockchain by [26]. Additionally, [27] presented a Blockchain-based calculated construction that gives an explanation for primary squares of the actual Web concerning the substitution of significant worth and genuine resources in strategic frameworks and decentralized control structures [27].
3. Methodology
3.1. Analysis of the existing system
From the information gathered plainly, most Nigerian colleges experience the ill effects of digital assaults, for example, unapproved admittance to understudies or staff records, control of results without regard for anyone else, and in some cases for monetary profits and other noxious inclinations by the programmer. Subsequently, there is a requirement for pressing upgrades which can be accomplished through the mix of a portion of the components of blockchain Innovation like decentralization, SHA-256 encryption, approval, and straightforwardness to work on the security of the framework.
The current framework utilizes a customer server design. A customer/server engineering is a unified design where every one of the records of information dwells on a solitary P.C., and it is powerless against assaults, and in case of an assault, everything information may be lost in light of the fact that there is no reinforcement server.
- Explicit issues related to the current framework include:
- Overloaded servers when there are incessant concurrent customer demands, server seriously get over-burden, framing gridlock.
- vulnerability to assaults because of complete centralization of framework.
- lack of approval of records.
- All clients are absolutely subject to the maker’s information base because of centralization.
- Impact of a brought together organization: since it is concentrated, if a basic server fizzles, customer demands are not refined. Accordingly, customer server comes up short on the vigor of a decent organization.
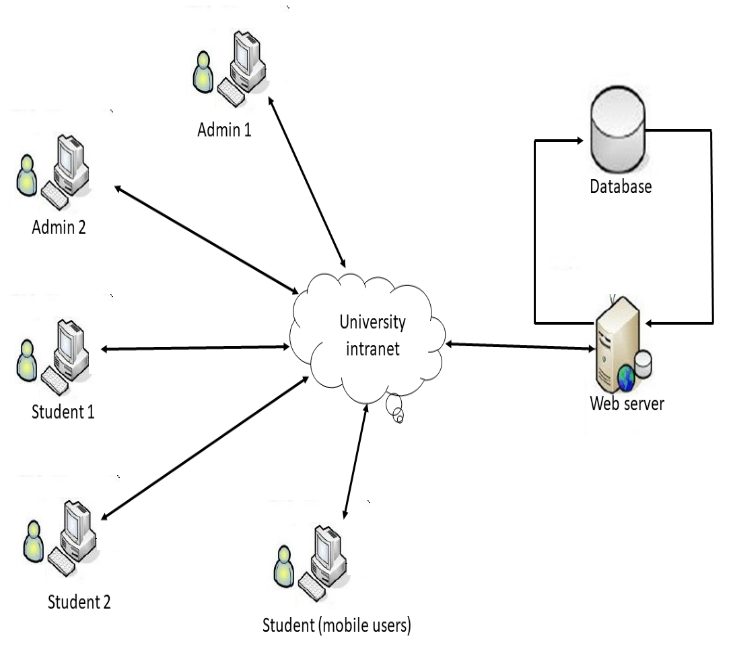
3.2. Proposed system
For the framework to fulfill the necessary guideline of in-weakness to assaults, there is a need to further develop the framework security, effectively open and be blockchain-like framework; it should be a blended organization design. Blockchain is totally decentralized with a “distributed” network design (that is, there is no focal control, and the hubs have equivalent control on the organization) dissimilar to the current college framework which is generally a concentrated framework running on a customer server network engineering.
Thusly, to accomplish the coordination of the blockchain into the college framework, there should be a think twice about both sides. The proposed framework in this exploration is a blended engineering, the mix of shared design and customer server engineering.
Un-like a blockchain framework there is a type of focal control by the chairman, the director can transfer records and make changes in the framework, the head can see the records and subtleties of the understudies and can likewise alter the understudies profile, yet a non-manager can’t adjust, change or controls any record or data on the framework. The understudies can only login to the framework to see their outcome and alter their profile which is approved by the blockchain. Complete components of blockchain innovation can’t be incorporated into the college framework, just about scarcely any significant provisions like SHA-256 encryption, record approval, straightforwardness and decentralization.
Because of Blockchain permanence, decentralization, circulation and agreement, blockchain gives upgraded security [28]. They see that chronicled information change will be unrealistic, and constant new information will be difficult to control as it is divided between all blockchain hubs with modification effortlessly recognized, followed and observed, forestalling misrepresentation and abuse. Blockchain can give both security and protection. However, with every one of the current dangers, blockchain is safer than the current concentrated framework
The availability of various elements in the proposed design in figure 3.1 depends on blockchain which gives efficient records stockpiling, sharing, and certification, which is made out of training foundations, consortium blockchain, capacity server, and the system administration.
3.2.1. Education Institutions
As the elements compared to the blockchain part hubs, instructive organizations are the fundamental assortment of information stockpiling and sharing on the blockchain.
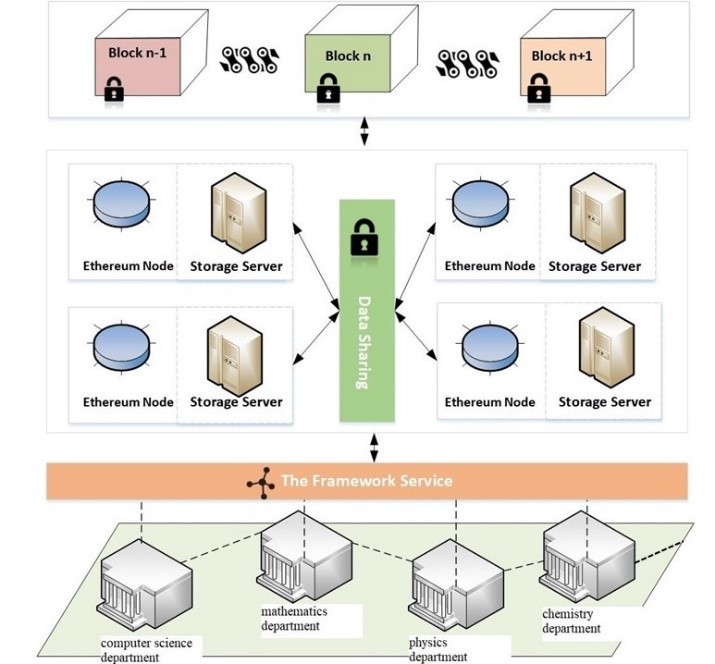
3.2.2. Consortium Blockchain
The pre-owned consortium blockchain is liable for putting away the synopsis data of scrambled records. Once more, Ethereum is taken on to carry out the consortium blockchain. The savvy contracts are sent to control the capacity and recovery of information.
3.2.3. Storage Server
The first records and files are encoded and put away in the capacity server. Xampp information base is picked as the capacity server to efficiently store and recover information and backing scrambled capacity of files.
3.2.4. The Framework Service
Contains a bunch of accessible utilitarian modules, doesn’t store any recorded data and offers types of assistance to hubs or clients as Relaxing APIs.
The proposed plan can be profoundly coordinated into the capacity, sharing and the board of instructive records.
3.3. System design
The framework configuration characterizes the plan, parts modules, interface and information for a framework that fulfill explicit necessities. The framework configuration permits the client gain an itemized comprehension of how the framework capacities.
It fosters the structural detail needed to assemble a framework or item.
The between network of various modules in the proposed framework engineering present in figure 3.1 gives a complete comprehension of the proposed framework design.
The Executives in various divisions transfer understudy records and information into the structure administration (the college framework) as data sources, this present data’s transition to the capacity servers where they are being put away. The associations between the capacity server and blockchain is a vehicle for sending data to the blockchain for approval and SHA-256 encryption. After the data is being gotten to by the blockchain, it goes through approval and SHA-256 encryption, and afterward, the information is being send back to the server or information sharing Center module. The information-sharing Center module then, at that point, gives the college structure administration admittance to this data however in SHA-256 scrambled structure. The scrambled data must be seen by various division yet can’t be changed on the grounds that the SHA-256 calculation produce irreversible and one-of-a-kind hashes. The bigger the quantity of potential hashes, the more modest the possibility that two qualities will make a similar hash.
From the college structure administration (framework), various divisions in the instructive foundation then, at that point, gains admittance to see this data.
The managers in various divisions are the just once fit for survey and making changes to this current data’s. The understudies can just view their outcomes and deal with their profile.
3.4. Data Security Framework using modified RSA Encryption Technique
Given that ‘n’ = modulus, Փ(n) = totient function, ‘e’ = Public Key functionality, ‘f’ = transform the value of Public Key functionality, ‘d’ = Private Key which is also the function the modulus, ‘C’ = encrypted using the transformed ‘f’ value, N = message in plain form, D = decrypted message.
A. Key Generation
- Select large prime numbers p and q.
- Obtain product n =p*q.
- Obtain product n = (p-1) *(q-1)
- Get e based on the following conditions {p> e >Փ(n), coprime Փ(n) and n} and gcd [e, Փ(n)] = 1
- Make a random selection ‘e’ from the list
- Compute f= ((e*2) +1).
- Make a selection of d from the relation {de modՓ(n) = 1}
- Send the Public Key (f, n) Where ‘f’ is serving as the new Public Key which is expected to hide the original ‘e’ value.
- Send Private key (d, n)
B. For data encryption
C = M((e*2) +1) mod(n)
C. For decryption at the receiving end
D = Cd mod(n)
Explanation: Observed that in the modified RSA Algorithm above, the public key functionality ‘e’ has been tempered with by transforming ‘e’ to ‘f’= (e*2)+1 in bid to obtained an improved security for the student data that is less vulnerable to factorization attack for malicious purpose (due to the additional second security layer obtained by transforming ‘e’ to ‘f’). In this case, students data on transit in a network or at rest in the server is protected to a reasonable extent. Essentially, the existing RSA encryption that depends on public key ‘e’ has been strengthened in the modified RSA by transforming the ‘e’ to an additional security layer ‘f’ to effectively protect student data in terms of confidentiality, integrity and authenticity.
Explanation: Observed that in the modified RSA Algorithm above, the public key functionality ‘e’ has been tempered with by transforming ‘e’ to ‘f’= (e*2)+1 in bid to obtained an improved security for the student data that is less vulnerable to factorization attack for malicious purpose (due to the additional second security layer obtained by transforming ‘e’ to ‘f’). In this case, students data on transit in a network or at rest in the server is protected to a reasonable extent. Essentially, the existing RSA encryption that depends on public key ‘e’ has been strengthened in the modified RSA by transforming the ‘e’ to an additional security layer ‘f’ to effectively protect student data in terms of confidentiality, integrity and authenticity.
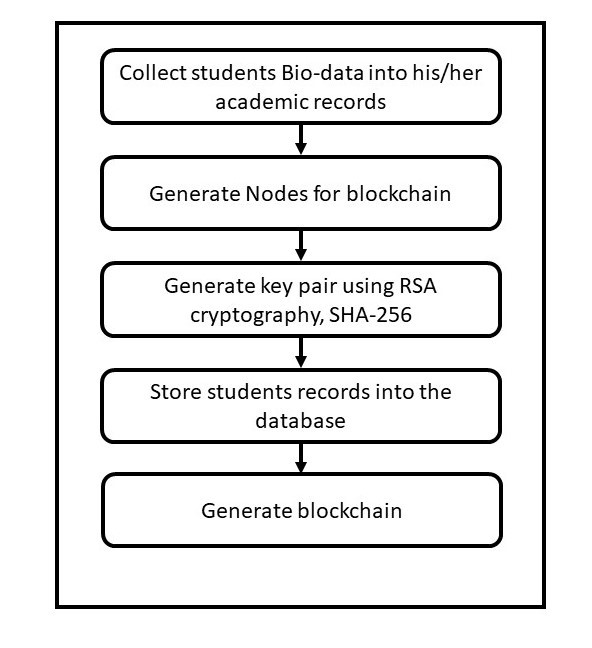
3.5. System Design Specification
Framework particular can be formal or casual. The proper framework determination is utilized in this exploration. It is a sort of framework particular that depicts different part of the framework verbally. Casual framework particular can likewise utilize graph to complete framework plan detail. In any case, it isn’t obligatory to utilize graphs given the portrayal of the framework is all around given.
In the mean time, the major useful necessity detail of the framework is that it should confirm exchange and encode records utilizing SHA-256 encryption highlights. The framework configuration comprises of interface determination, program detail and information base particular.
3.5.1. Interface specification
The interface is where data can be supplied to and out the system. It has an interface for both the admin and customer login, the interface to create and an account for the customer and for the customer to transfer funds to the other customer, interface for viewing profiles and transactions.
3.5.2. Database specifications
The database consists of admin/bankers, customers and transactions(passbook). The field of the database should be according to the information needed in the fields. The names and other personal details should have variable characters.
3.5.3. Input Interface Design
The input interfaces of the application consist of some input functionality which can be accessible by the administrator and user or customer of the system.
The input design of this software includes
- Administrator login: is the first page the admin sees (index page) when the web system loads on the browser, admin have to input his or her username and password and when he clicks the login button, the input is authenticated before the admin can access the admin home page, where the admin can manage students record. The admin manages the students record by performing actions such as: creating, updating, and editing students record.
- Customer login: is the first page the student sees (index page) when the web system loads on the browser, student have to input his or her username and password. The input is authenticated before the student can access the customer home page, where the student can edit his or her profile.
- Create students (this functionality is only available to the administrator): in this input page, the admin creates a profile for the students, the genesis block is also created when the student profile is created. The admin inputs the student details (such as name, age, date of birth and other relevant information) in this page and submit in other to create the student profile.
3.6. Database Design
Files held in this project are made up of different data types. These types are integer, Character, Double, Date, etc. Some of the files used are designed and linked with database. Also, in the project design, MySQL database was used. Below is the database specification for the files used.
Table 1: Students; The design layout of database tables for students
File Name | Data Type | Size | Relation |
Student_id | Int | 11 | Primary key |
First_name | Varchar | 30 | Not null |
Last_name | Varchar | 30 | Not null |
Gender | Varchar | 10 | Not null |
Faculty | Int | 20 | Not null |
Department | Int | 20 | Not null |
DOB | Varchar | 30 | Not null |
Nationality | Varchar | 20 | Not null |
State | Varchar | 30 | Not null |
LGA | Varchar | 30 | Not null |
Marital status | Int | 15 | Not null |
Email id | Int | 20 | Not null |
Phone no. | Int | 11 | Not null |
Uname | Varchar | 30 | Foreign key |
Pwd | Varchar | 30 | Foreign key |
Table 2: ADMINISTRATOR: the design layout of database tables for admin
Filename | Data Type | Size | Relation |
Id | Int | 11 | Primary key |
Username | Char | 25 | Foreign key |
Pwd | Char | 25 | Foreign key |
Table 3: RECORD/RESULTS: the design layout of database tables for students’records
File name | Data type | Size | Relation |
Record_id | Int | 11 | Primary key |
Course code | Int | 10 | Not null |
Course title | Int | 50 | Not null |
Credit unit | Int | 11 | Not null |
GP | Int | 11 | Not null |
CGPA | Int | 11 | Not null |
Remark | Int | 11 | Not null |
PRecordhash | Varchar | 64 | Not null |
Recordhash | Varchar | 64 | Not null |
3.7. System Development
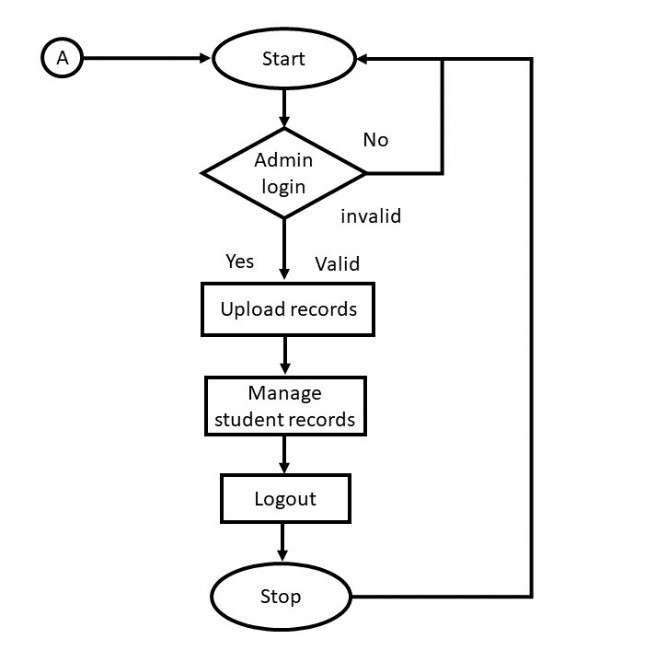
Flow chart shows how the data flow in the system. Flow chart depicting the operation of this system and show the operational flows.
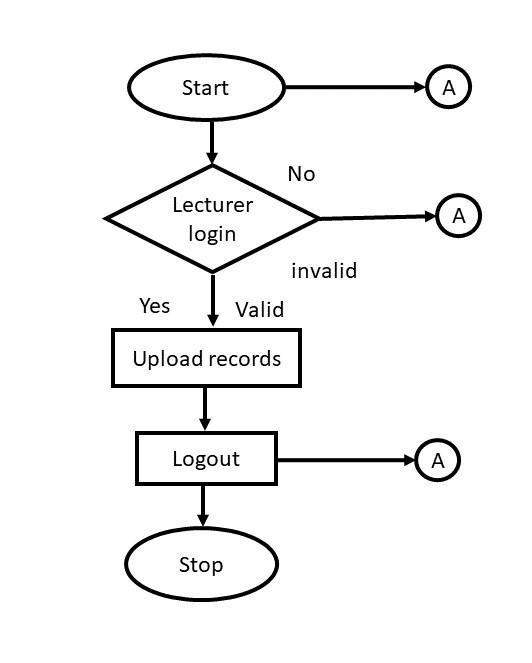
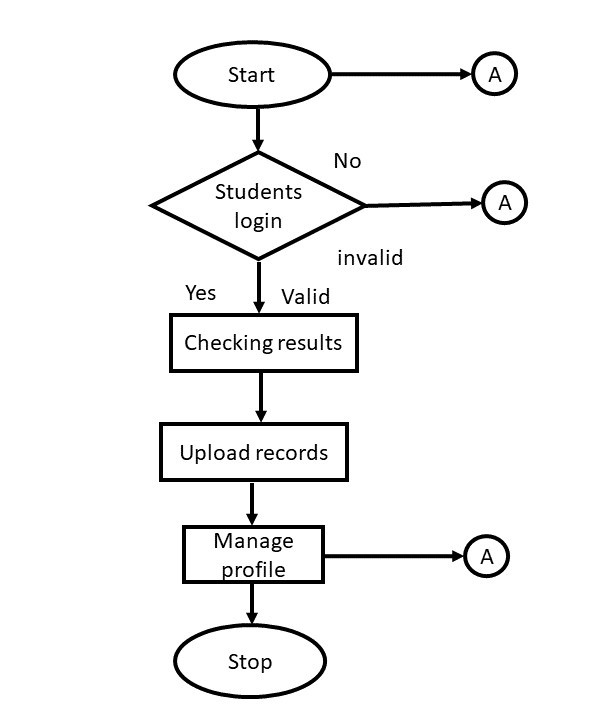
3.8. System Modeling Using Unified Modeling Language (UML).
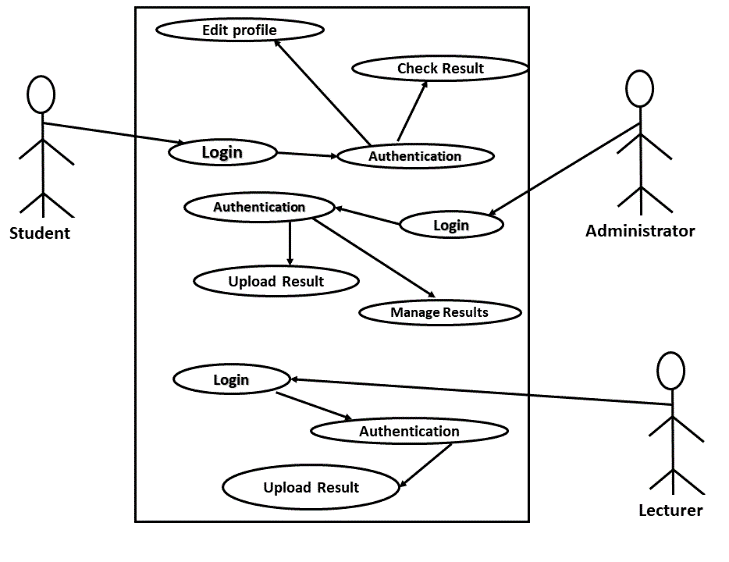
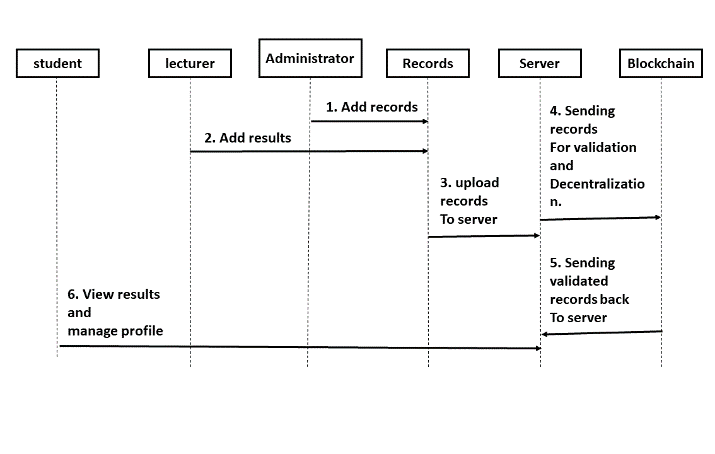
Various UML tools were used to model the basic functionalities required for a working system. More specifically for this research, UML use cases, class diagram, sequence diagram and entity-relation (E-R) diagram were used to model the system.
The UML use case for the system is as shown in Figure 7 below:
The sequence diagram used to model basic artifacts of the system is given in Figure 8 below:
The class diagram that was used in modelling different object classes for the system is as displayed in Figure 9 below:
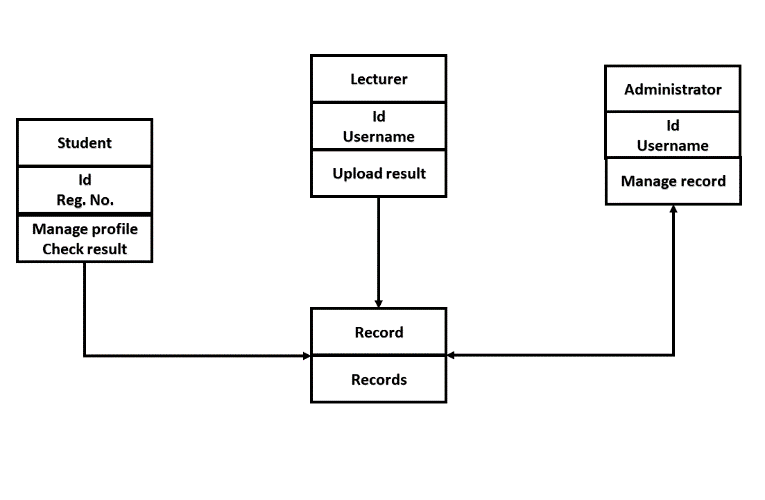
The entity relationship model for the proposed system is described in Figure 10 below:
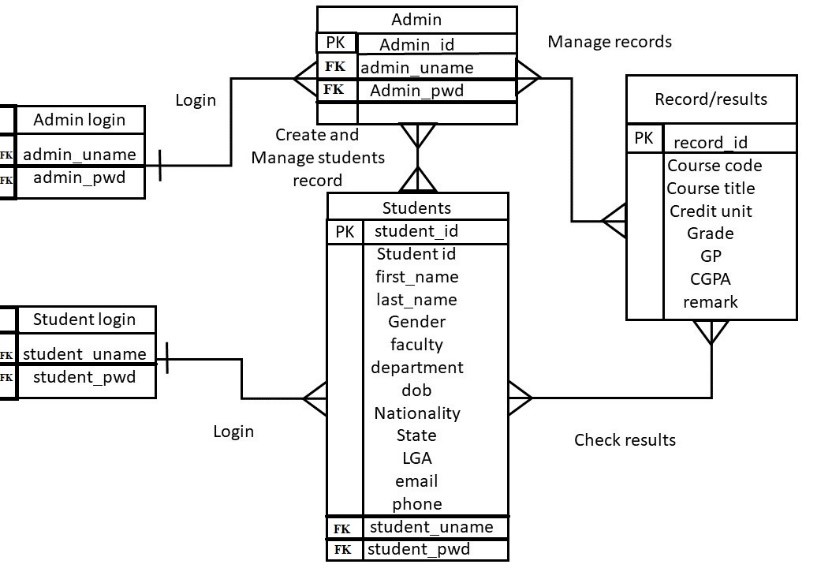
3.9. Technologies for Development
The developmental tools and technologies used include PHP/MySQL for the database because PHP/MySQL is more secure and robust than another database, it is easy to implement, and I have more experience with PHP/MySQL.
The system was developed using vs code. HTML, JAVASCRIPT and CSS are used to develop the User Interface. PHP (Hypertext Preprocessor) was the programming language used. PHP is a scripting language designed specifically for use on the Web.
4. Implementation
4.1. System Implementation
In this section the modelled system was implemented where details were presented for a smooth execution.
The integration of blockchain-enabled framework for securing students record was a success. After several tests run on the developed system. The administrator can create the genesis block by adding students’ function, which is creating students’ profile.
The institution framework is secure and reliable since students’ records are encrypted, and the system is decentralized. Therefore, the aim of the study is achieved.
4.2. Discussion
Blockchain has been accepted in many areas such as banking system, health care, supply chain production and academic institutions.
The results of this research is the blockchain-enabled system for data storage, security and sharing of students record in educational institution. The results obtained shows that the use of blockchain technology will be a great improvement in universities.
From the literature review and related works of this research, the implementation of blockchain in educational institution to improve learning always end up with issues like difficulty of point of synchronization in IoT, inability to tamper with any record after being stored in the system. But mostly, blockchain has not been widely used in academic institutions or universities especially in most African countries like Nigeria.
This research focuses on the practical aspect of blockchain implementation, from the results of the implementation this research eliminates the need of any difficulty of point of synchronization and tamper of proof. The implemented system provides a sharing medium whereby an administrator from the computer science department is capable of viewing students record from mathematics or physics but cannot tamper or change those records.
The system provides an efficient and maximum data storage, sharing of students records, and security using RSA and SHA-256 encryption to record and encrypt students records.
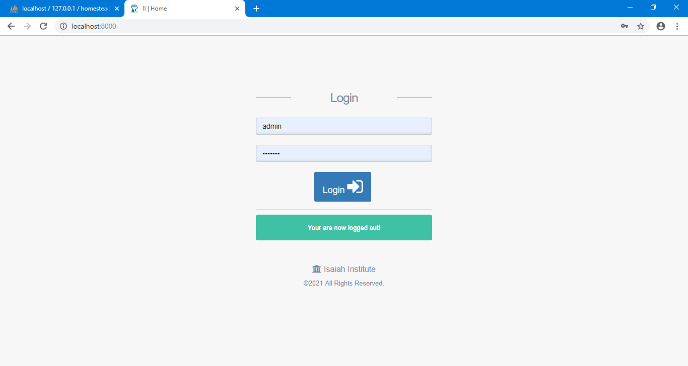
Figure 11 shows vividly the administrators login page, where the administrators can get access into the university management system to store and manage students records and perform other activities. This is the administrators gateway into the system.
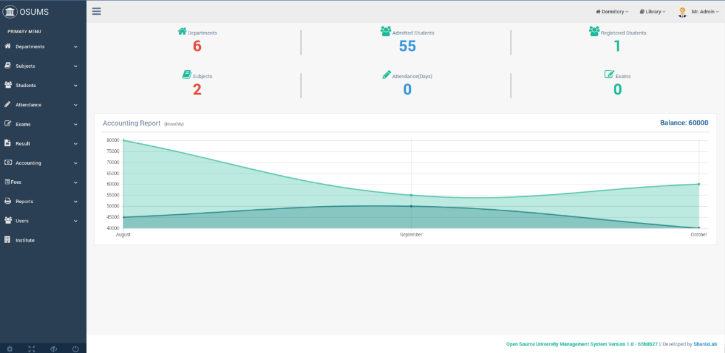
Figure 12 the home page or dashboard of the system. After the administrator has get accessed to the system, this landing page is the administrator’s dashboard. Here the administrator can see the number of departments, number of students, number of subjects, number of registered courses and other related activities that are contained or stored on the system.
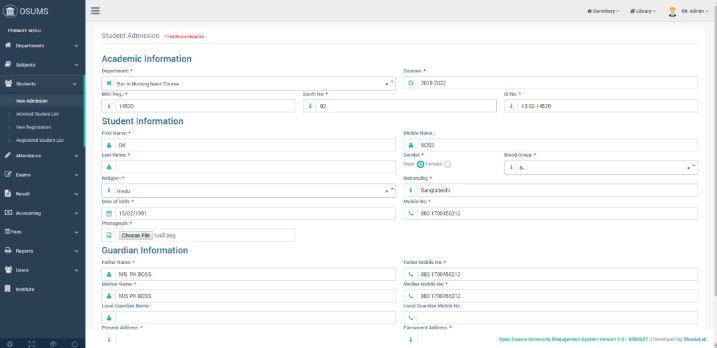
Figure 13 is an interface which shows a clear view of the create student profile for new students by the administrator. This is where the administrator creates profiles for new students. The administrator is the only person capable of creating a students’ profile in the university system. The fields consist of different data to be obtained from the newly admitted student.
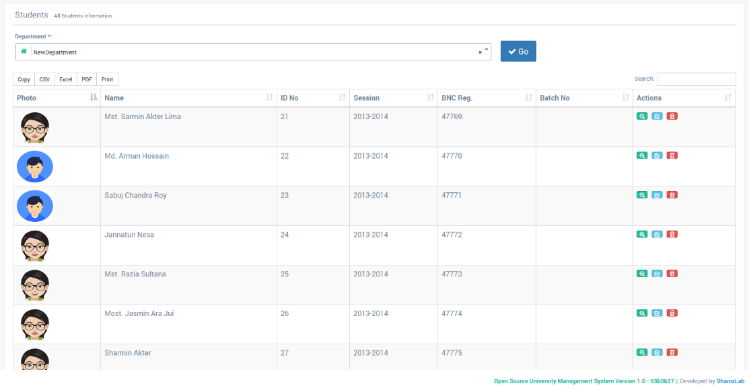
Figure 14 shows different students of different department, this interface allows administrators of different department to view the records and details of student from different departments. Here, an administrator from the computer science department can view the results of a student from mathematics and physics or any other department as administrators from other departments too can view the records of students from another department.
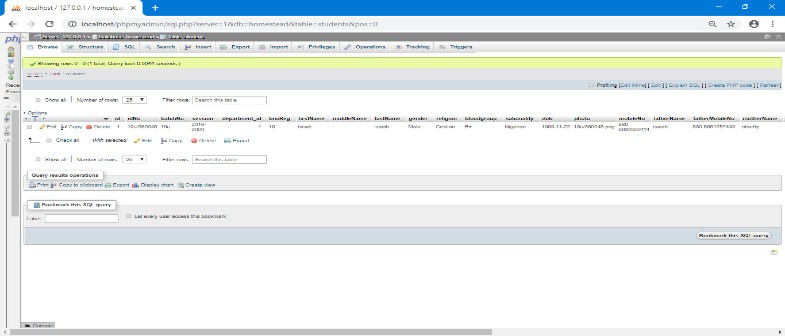
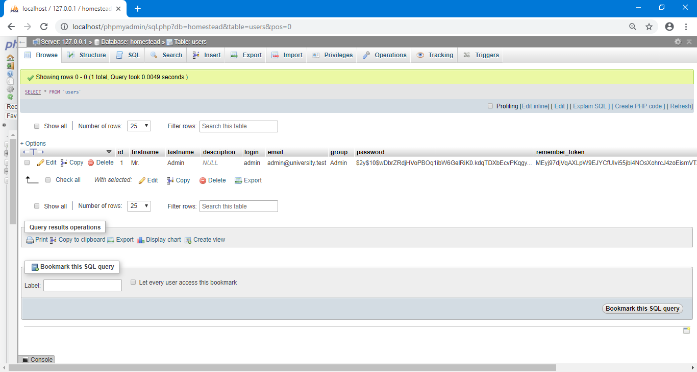
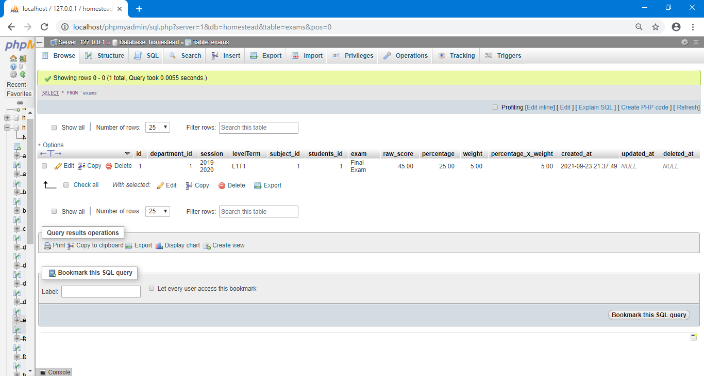
Figure 15 shows the student profile File System Implementation; the interface is the student table as it appears in the database. Figure 16 shows the Administrator File System Implementation; the interface is the administrators table as it appears in the database. Figure 17 shows the Records (Exams) File System Implementation the interface is the student records as it appears in the database where the students’ data is being stored.
5. Conclusion
The point of this review is to survey IoT and perceive how it tends to be Coordinated with Square chain innovation in college gateways in a bid to further develop security of information store, plan, study and carry out a framework that will upgrade blockchain-empowered. A tremendous degree of potentials for the institutions to take advantage of the implementation of a blockchain-empowered framework. This innovation can specify college development and advancement. The degree of innovation in terms of progress which is taking in division in present day have been both strengthen and overwhelming, in terms of examining how many surges of mechanical developments with immerse specialization and organized information world.
The review explored the utilization of blockchain-empowered instructive organization and the investigation discovers that clients of the proposed gateway system expect; admittance to grades, profile and different provisions on the entry; clients need more admittance to the entryway. In this way, it is reasoned that reviews on client necessities of blockchain-empowered training foundation ought to be consistent and at stretches to get criticism from clients by administrators of the gateway with the end goal of meeting client prerequisites for better usability. It may be insufficient to start the framework and similar services without taking into consideration, client discernments, prerequisites, needs and difficulties, all of which have the tendency to add to the overall expectations of the organization being upgraded in terms of learning and to simultaneously understudy suitably of students’ records. It is much more efficient to lead comparable analysis in this 21st century electronic driven climate.
Blockchain has shown its capacity for modifying conventional organization with its key attributes: decentralization, persistency, secrecy and auditability. In this research, a far-reaching outline on blockchain is presented. An outline of blockchain advances including blockchain engineering and key qualities of blockchain is presented. Also, an examination of the regular agreement algorithms is utilized in blockchain.
- W. Villegas-Ch; M. Roman-Carnizares; X. Palacious-Pacheco. Improvement of an online educational model with the integration of machine learning and data analysis in LMS. Appl. Sci. 2020, vol. 10, pp. 5371, doi: 10.3390/app10155371.
- P. Butz; B. Tauscher. Emerging technologies: Chemical aspects. Food Res. Int. 2002, vol. 35, pp. 279–284, doi: 10.1016/S0963-9969(01)00197-1. [CrossRef]
- F. Montori; L. Bedogni; L. Bononi. A Collaborative Internet of Things Architecture for Smart Cities and Environmental Monitoring. IEEE Internet Thing J. 2018, vol. 5, pp. 592–605, doi: 10.1109/JIOT-IEEE.2017.2720855. [CrossRef]
- M. Alvarez-Campana; G. López; E. Vázquez; V. A. Villagrá; J. Berrocal; Smart CEI moncloa: An iot-based platform for people flow and environmental monitoring on a Smart University Campus. Sensors 2017, 17, 2856, doi 10.3390/j.s2017.1712228
- L. Catarinucci; D. De Donno; L. Mainetti; L. Palano; L. Patrono; M. L. Stefanizzi; L. Tarricone. An IoT-Aware Architecture for Smart Healthcare Systems. IEEE Internet Things J. 2015, 2, 515–526, doi: 10.1109/JIOT.2015.2417684. [CrossRef]
- H. Y. Shwe T. K. Jet; P. H. J. Chong. An IoT-oriented data storage framework in smart city applications. In Proceedings of the International Conference on Information and Communication Technology Convergence, ICTC 2016, Jeju, Korea, 19–21 October 2016; pp. 106–108, doi: 10.1109/ICTC.2016.7763446. [CrossRef]
- S. Madakam; R. Ramaswamy; S. Tripathi. Internet of Things (IoT): A Literature Review. J.Comput. Commun. 2015, vol. 3, pp. 164–173, doi: 10.4236/jcc.2015.35021. [CrossRef]
- P. Bellagente; P. Ferrari; A. Flammini; S. Rinaldi. Adopting IoT framework for Energy Management of Smart Building: A real test-case. In Proceedings of the IEEE 1st International Forum on Research and Technologies for Society and Industry, Turin, Italy, 16–18 September 2015; pp. 138–143, dol: 10.1109/RTSI.IEEE.2015.7325084
- M. Batty; K. W. Axhausen; F. Giannotti; A. Pozdnoukhov; A. Bazzani; N. Wachowicz; G. Ouzounis; Y. Portugali. Smart cities of the future. Eur. Phys. J.Spec. Top.2012,214 pp. ,481–518, doi: 10.1140/epjst/e2012-01703-3.
- J. Zhou; Y. Zhou; B. Wang; J. Zang. Human–Cyber-Physical Systems (HCPSs) in the Context of New-Generation Intelligent Manufacturing. Engineering 2019, vol. 5, pp. 624–636, doi: 10. 1016/j.eng.2019.07.015.
- J. Zhou; Y. Zhou; B. Wang; J. Zang; L. Meng. Toward New-Generation Intelligent Manufacturing. Engineering 2018, 4, 11–20, doi: 10.1016/j.eng.2018.01.002. [CrossRef]
- W. Baicun; Z. Jiyuan; Q. Xianming; D. Jingchen; Z. Yanhong. Research on New-Generation Intelligent Manufacturing based on Human-Cyber-Physical Systems. Chin. J. Eng. Sci. 2018, 20, 29, 10.15302/J-SSCAE-2018.04.006.
- M. Aazam; I. Khan; A. A. Alsaffar; E. N. Huh. Cloud of Things: Integrating Internet of Things and cloud computing and the issues involved. In Proceedings of the 11th International Bhurban Conference on Applied Sciences and Technology, IBCAST, Islamabad, Pakistan, 14–18 January 2014; pp. 414–419, doi: 10.1109/IBCAST.2014.6778179.
- Y. Mahmoodi; S. Reiter; A. Viehl; O. Bringmann; W. Rosenstiel. Attack surface modeling and assessment for penetration testing of IoT system designs. In Proceedings of the 21st Euromicro Conference on Digital System Design (DSD), Prague, Czech Republic, 29–31 August 2018; pp. 177–181, doi: 10.1109/DSD.2018.00043
- H. Suo; J. Wan; C. Zou; J. Liu. Security in the internet of things: A review. In Proceedings of the International Conference on Computer Science and Electronics Engineering, ICCSEE, Hangzhou, China, 23–25 March 2012; Volume 3, pp. 648–651, 10.1109.ICCSEE.2012.373.
- P. P. Ray. A survey of IoT cloud platforms. Future Comput. Inf. J. 2016, vol. 1, pp. 35–46, doi: 10.1013/j.fcij.2017.02.001
- R. Khan; S. U. Khan; R. Zaheer; S. Khan. Future internet: The internet of things architecture, possible applications and key challenges. In Proceedings of the 10th International Conference on Frontiers of Information Technology, FIT 2012, Islamabad, India, 17–19 December 2012; pp. 257–260, doi: 10.1109/FIT.2012.53
- M. Liu; L. Li. The construction of smart campus in universities and the practical innovation of student work. In Proceedings of the International Conference on Information Management & Management Science, Chengdu, China, 24–26 August 2018; pp. 154–157, doi: 10.1145/IMMS.3277139.3278307
- W. Villegas-Ch; X. Palacios-Pacheco; S. Luján-Mora. Application of a Smart City Model to a Traditional University Campus with a Big Data Architecture: A Sustainable Smart Campus. Sustainability 2019, vol. 11, pp. 2857, doi: 10.3390/su11102857
- H. Wang; Z. Zheng; S. Xie; H. N. Dai; X. Chen. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352, doi: 10.1504/ijwgs.2018.095647. [CrossRef]
- D. Minoli; B. Occhiogrosso. Blockchain mechanisms for IoT security. Internet Things 2018, 1–2, pp. 1–13, doi: 10.1016/j.iot.2018.05.002. [CrossRef]
- A. D. Dwivedi; G. Srivastava; S. Dhar; R. Singh. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 2019, 19, 326, doi: 10.3390/s19020326. [CrossRef]
- V. L. Uskov; J. P. Bakken; A. Pandey. Smart University Taxonomy: Features, Components, Systems. In Smart Education and e-Learning; Springer: Cham, Switzerland, 2016; Volume 59, pp. 3–14, doi: 10.1007/978-3-319-39690-3_1. [CrossRef]
- N. Kamal, M.H.M. Saad, C.S. Kok, and A. Hussain, “Towards Revolutionizing STEM Education via IoT and Blockchain Technology,” International Journal of Engineering and Technology (UAE), Vol. 7, No. 4, 2018, pp. 189-192, doi: 10.14419/ijet.v7i4.11.20800.
- K. Fan, S. Sun, Z. Yan, Q. Pan, H. Li, and Y. Yang, “A Blockchain-Based Clock Synchronization Scheme in IoT,” Future Generation Computer Systems, Vol. 101, December 2019, pp. 524-533, doi: 10.1016/j.future.2019.06.007.
- G. Khan, S. Jabeen, M.Z. Khan, M.U.G. Khan, and R. Iqbal, “Blockchain-Enabled Deep Semantic Video-to-Video Summarization for IoT Devices,” Computers & Electrical Engineering, Vol. 81, 2020, art. 106524, doi: 10.1016/j.compeleceng.2019.106524.
- T. Meyer, M. Kuhn, and E. Hartmann, “Blockchain Technology Enabling the Physical Internet: A Synergetic Application Framework,” Computers & Industrial Engineering, Vol. 136, October 2019, pp. 517, doi: 10.106/j.cie.2019.07.006
- H. Hassani, and E. S. Silva (2018). Forecasting U.K. Consumer Price Ination Using Ination Forecasts. Records in Economics, in Press. doi: 10.1016/j.rie.2018.07.001.
- Omega Sarjiyus, Israel Isaiah, “A Vendor-Agnostic Multi-Cloud Integration Framework Using Boomi and SAP BTP”, Journal of Engineering Research and Sciences, vol. 4, no. 12, pp. 1–14, 2025. doi: 10.55708/js0412001
- Omega Sarjiyus, Israel Isaiah, “Unveiling the Evolving Threat Landscape of Distributed Denial-of-Service (DDoS) Attacks Methodology and Security Measures”, Journal of Engineering Research and Sciences, vol. 4, no. 10, pp. 9–20, 2025. doi: 10.55708/js0410002
- Omega Sarjiyus, Israel Isaiah, “AI-Enhanced Endpoint Compliance and Automated Vulnerability Management Framework for Essential Government Infrastructure”, Journal of Engineering Research and Sciences, vol. 4, no. 8, pp. 18–23, 2025. doi: 10.55708/js0408002
- Omega Sarjiyus, Israel Isaiah, “Secure Anonymous Acknowledgments in a Delay-Tolerant Network”, Journal of Engineering Research and Sciences, vol. 3, no. 11, pp. 24–30, 2024. doi: 10.55708/js0311002
- Omega Sarjiyus, Israel Isaiah, “Navigating the Autonomous Era: A Detailed Survey of Driverless Cars”, Journal of Engineering Research and Sciences, vol. 3, no. 10, pp. 21–36, 2024. doi: 10.55708/js0310003
